Ingress介绍
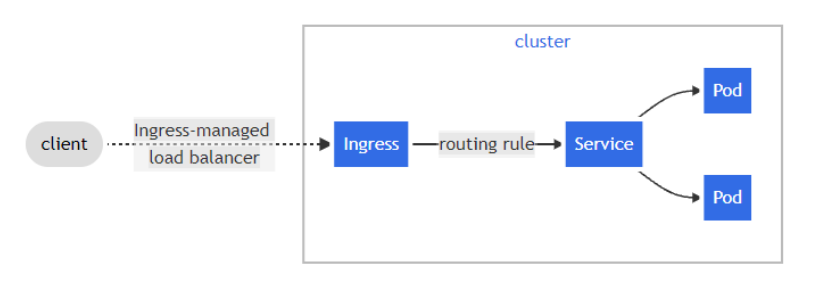
Ingress将来自集群外部的 HTTP 和 HTTPS 路由暴露给集群 内的服务。流量路由由 Ingress
资源上定义的规则控制。
Ingress 其实就是从 Kuberenets 集群外部访问集群的一个入口,将外部的请求转发到集群内不同的 Service 上,其实就相当于 nginx、haproxy 等负载均衡代理服务器,但是只使用nginx这种方式有很大缺陷,每次有新服务加入的时候需要改nginx 配置,不可能让我们去手动更改或者滚动更新前端的nginx-pod,那我们再加上一个服务发现的工具比如consul,Ingress 实际上就是这样实现的,只是服务发现的功能自己实现了,不需要使用第三方的服务了,然后再加上一个域名规则定义,路由信息的刷新依靠 Ingress Controller 来提供。
下面简单示例:
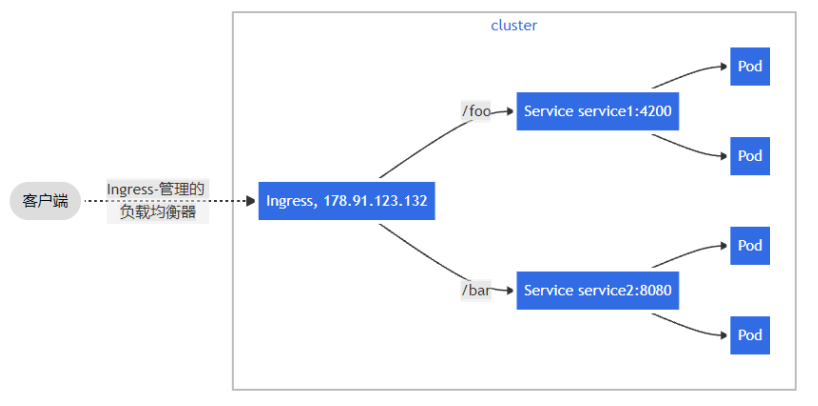
其中 Ingress 将其所有流量发送到一个 Service:
Ingress 可以配置为向服务提供外部可访问的 URL、负载平衡流量、终止 SSL/TLS 并提供基 于名称的虚拟主机。
一个入口控制器负责履行入口,通常有一个负载均衡器,虽然它也可以 配置您的边缘路由器或额外的前端,以帮助处理流量。
Ingress 不会公开任意端口或协议。
向 Internet 公开 HTTP 和 HTTPS 以外的服务通常使用 Service.Type=NodePort 或 Service.Type=LoadBalancer 类型的服务。
服务的区别
service只能通过四层负载就是ip+端口的形式来暴露
- NodePort:会占用集群机器的很多端口,当集群服务变多的时候,这个缺点就越发明显
- LoadBalancer:每个Service都需要一个LB,比较麻烦和浪费资源,并且需要 k8s之外的负载均衡设备支持
ingress可以提供7层的负责对外暴露接口,而且可以调度不同的业务域,不同的url访问路径的业务流量。
- Ingress:K8s 中的一个资源对象,作用是定义请求如何转发到 service 的规则
- Ingress Controller:具体实现反向代理及负载均衡的程序,对Ingress定义的规则进行解析,根据配置的规则来实现请求转发,有很多种实现方式,如 Nginx、Contor、Haproxy等
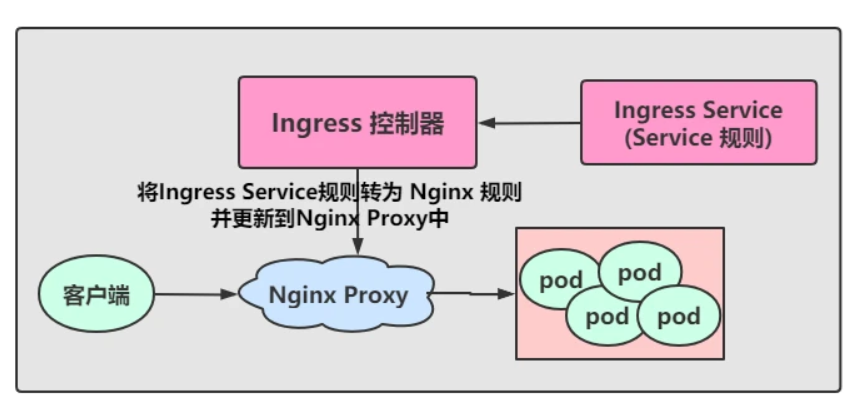
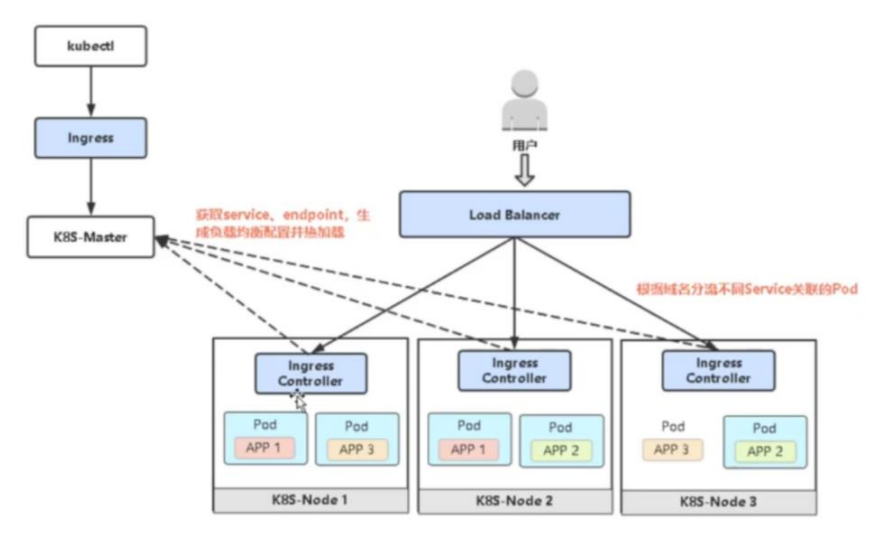
工作原理
- 用户编写 Ingress Service规则, 说明每个域名对应 K8s集群中的哪个Service
- Ingress控制器会动态感知到 Ingress 服务规则的变化,然后生成一段对应的Nginx反向代理配置
- Ingress控制器会将生成的Nginx配置写入到一个运行中的Nginx服务中,并动态更新
- 然后客户端通过访问域名,实际上Nginx会将请求转发到具体的Pod中,到此就完成了整个请求的过程
ingress安装
已经自建好阿里云镜像可以直接部署ingress-nginx
提前下载镜像
docker pull registry.cn-hangzhou.aliyuncs.com/yutao517/ingress_nginx_controller:v1.1.0 docker tag registry.cn-hangzhou.aliyuncs.com/yutao517/ingress_nginx_controller:v1.1.0 k8s.gcr.io/ingress-nginx/controller:v1.1.1 docker pull registry.cn-hangzhou.aliyuncs.com/yutao517/kube_webhook_certgen:v1.1.1 docker tag registry.cn-hangzhou.aliyuncs.com/yutao517/kube_webhook_certgen:v1.1.1 k8s.gcr.io/ingress-nginx/kube-webhook-certgen:v1.1.1
下载deploy.yaml文件
wget https://download.yutao.co/mirror/deploy.yaml
修改deploy.yaml文件
将文件中的,依赖 ingress_nginx_controller:v1.1.0 镜像的版本,修改 为 ingress_nginx_controller:v1.1.1
修改之后的配置
apiVersionv1 kindNamespace metadata nameingress-nginx labels app.kubernetes.io/nameingress-nginx app.kubernetes.io/instanceingress-nginx ---# Source: ingress-nginx/templates/controller-serviceaccount.yamlapiVersionv1 kindServiceAccount metadata labels helm.sh/chartingress-nginx-4.0.10 app.kubernetes.io/nameingress-nginx app.kubernetes.io/instanceingress-nginx app.kubernetes.io/version1.1.0 app.kubernetes.io/managed-byHelm app.kubernetes.io/componentcontroller nameingress-nginx namespaceingress-nginx automountServiceAccountTokentrue---# Source: ingress-nginx/templates/controller-configmap.yamlapiVersionv1 kindConfigMap metadata labels helm.sh/chartingress-nginx-4.0.10 app.kubernetes.io/nameingress-nginx app.kubernetes.io/instanceingress-nginx app.kubernetes.io/version1.1.0 app.kubernetes.io/managed-byHelm app.kubernetes.io/componentcontroller nameingress-nginx-controller namespaceingress-nginx data allow-snippet-annotations'true'---# Source: ingress-nginx/templates/clusterrole.yamlapiVersionrbac.authorization.k8s.io/v1 kindClusterRole metadata labels helm.sh/chartingress-nginx-4.0.10 app.kubernetes.io/nameingress-nginx app.kubernetes.io/instanceingress-nginx app.kubernetes.io/version1.1.0 app.kubernetes.io/managed-byHelm nameingress-nginx rulesapiGroups'' resourcesconfigmaps endpoints nodes pods secrets namespaces verbslist watch apiGroups'' resourcesnodes verbsget apiGroups'' resourcesservices verbsget list watch apiGroupsnetworking.k8s.io resourcesingresses verbsget list watch apiGroups'' resourcesevents verbscreate patch apiGroupsnetworking.k8s.io resourcesingresses/status verbsupdate apiGroupsnetworking.k8s.io resourcesingressclasses verbsget list watch ---# Source: ingress-nginx/templates/clusterrolebinding.yamlapiVersionrbac.authorization.k8s.io/v1 kindClusterRoleBinding metadata labels helm.sh/chartingress-nginx-4.0.10 app.kubernetes.io/nameingress-nginx app.kubernetes.io/instanceingress-nginx app.kubernetes.io/version1.1.0 app.kubernetes.io/managed-byHelm nameingress-nginx roleRef apiGrouprbac.authorization.k8s.io kindClusterRole nameingress-nginx subjectskindServiceAccount nameingress-nginx namespaceingress-nginx ---# Source: ingress-nginx/templates/controller-role.yamlapiVersionrbac.authorization.k8s.io/v1 kindRole metadata labels helm.sh/chartingress-nginx-4.0.10 app.kubernetes.io/nameingress-nginx app.kubernetes.io/instanceingress-nginx app.kubernetes.io/version1.1.0 app.kubernetes.io/managed-byHelm app.kubernetes.io/componentcontroller nameingress-nginx namespaceingress-nginx rulesapiGroups'' resourcesnamespaces verbsget apiGroups'' resourcesconfigmaps pods secrets endpoints verbsget list watch apiGroups'' resourcesservices verbsget list watch apiGroupsnetworking.k8s.io resourcesingresses verbsget list watch apiGroupsnetworking.k8s.io resourcesingresses/status verbsupdate apiGroupsnetworking.k8s.io resourcesingressclasses verbsget list watch apiGroups'' resourcesconfigmaps resourceNamesingress-controller-leader verbsget update apiGroups'' resourcesconfigmaps verbscreate apiGroups'' resourcesevents verbscreate patch ---# Source: ingress-nginx/templates/controller-rolebinding.yamlapiVersionrbac.authorization.k8s.io/v1 kindRoleBinding metadata labels helm.sh/chartingress-nginx-4.0.10 app.kubernetes.io/nameingress-nginx app.kubernetes.io/instanceingress-nginx app.kubernetes.io/version1.1.0 app.kubernetes.io/managed-byHelm app.kubernetes.io/componentcontroller nameingress-nginx namespaceingress-nginx roleRef apiGrouprbac.authorization.k8s.io kindRole nameingress-nginx subjectskindServiceAccount nameingress-nginx namespaceingress-nginx ---# Source: ingress-nginx/templates/controller-service-webhook.yamlapiVersionv1 kindService metadata labels helm.sh/chartingress-nginx-4.0.10 app.kubernetes.io/nameingress-nginx app.kubernetes.io/instanceingress-nginx app.kubernetes.io/version1.1.0 app.kubernetes.io/managed-byHelm app.kubernetes.io/componentcontroller nameingress-nginx-controller-admission namespaceingress-nginx spec typeClusterIP portsnamehttps-webhook port443 targetPortwebhook appProtocolhttps selector app.kubernetes.io/nameingress-nginx app.kubernetes.io/instanceingress-nginx app.kubernetes.io/componentcontroller ---# Source: ingress-nginx/templates/controller-service.yamlapiVersionv1 kindService metadata annotations labels helm.sh/chartingress-nginx-4.0.10 app.kubernetes.io/nameingress-nginx app.kubernetes.io/instanceingress-nginx app.kubernetes.io/version1.1.0 app.kubernetes.io/managed-byHelm app.kubernetes.io/componentcontroller nameingress-nginx-controller namespaceingress-nginx spec typeNodePort externalTrafficPolicyLocal ipFamilyPolicySingleStack ipFamiliesIPv4 portsnamehttp port80 protocolTCP targetPorthttp appProtocolhttp namehttps port443 protocolTCP targetPorthttps appProtocolhttps selector app.kubernetes.io/nameingress-nginx app.kubernetes.io/instanceingress-nginx app.kubernetes.io/componentcontroller ---# Source: ingress-nginx/templates/controller-deployment.yamlapiVersionapps/v1 kindDeployment metadata labels helm.sh/chartingress-nginx-4.0.10 app.kubernetes.io/nameingress-nginx app.kubernetes.io/instanceingress-nginx app.kubernetes.io/version1.1.0 app.kubernetes.io/managed-byHelm app.kubernetes.io/componentcontroller nameingress-nginx-controller namespaceingress-nginx spec selector matchLabels app.kubernetes.io/nameingress-nginx app.kubernetes.io/instanceingress-nginx app.kubernetes.io/componentcontroller revisionHistoryLimit10 minReadySeconds0 template metadata labels app.kubernetes.io/nameingress-nginx app.kubernetes.io/instanceingress-nginx app.kubernetes.io/componentcontroller spec dnsPolicyClusterFirst containersnamecontroller imagek8s.gcr.io/ingress-nginx/controllerv1.1.1 imagePullPolicyIfNotPresent lifecycle preStop exec command/wait-shutdown args/nginx-ingress-controller --publish-service=$(POD_NAMESPACE)/ingress-nginx-controller --election-id=ingress-controller-leader --controller-class=k8s.io/ingress-nginx --configmap=$(POD_NAMESPACE)/ingress-nginx-controller --validating-webhook=:8443 --validating-webhook-certificate=/usr/local/certificates/cert --validating-webhook-key=/usr/local/certificates/key securityContext capabilities dropALL addNET_BIND_SERVICE runAsUser101 allowPrivilegeEscalationtrue envnamePOD_NAME valueFrom fieldRef fieldPathmetadata.name namePOD_NAMESPACE valueFrom fieldRef fieldPathmetadata.namespace nameLD_PRELOAD value/usr/local/lib/libmimalloc.so livenessProbe failureThreshold5 httpGet path/healthz port10254 schemeHTTP initialDelaySeconds10 periodSeconds10 successThreshold1 timeoutSeconds1 readinessProbe failureThreshold3 httpGet path/healthz port10254 schemeHTTP initialDelaySeconds10 periodSeconds10 successThreshold1 timeoutSeconds1 portsnamehttp containerPort80 protocolTCP namehttps containerPort443 protocolTCP namewebhook containerPort8443 protocolTCP volumeMountsnamewebhook-cert mountPath/usr/local/certificates/ readOnlytrue resources requests cpu100m memory90Mi nodeSelector kubernetes.io/oslinux serviceAccountNameingress-nginx terminationGracePeriodSeconds300 volumesnamewebhook-cert secret secretNameingress-nginx-admission ---# Source: ingress-nginx/templates/controller-ingressclass.yaml# We don't support namespaced ingressClass yet# So a ClusterRole and a ClusterRoleBinding is requiredapiVersionnetworking.k8s.io/v1 kindIngressClass metadata labels helm.sh/chartingress-nginx-4.0.10 app.kubernetes.io/nameingress-nginx app.kubernetes.io/instanceingress-nginx app.kubernetes.io/version1.1.0 app.kubernetes.io/managed-byHelm app.kubernetes.io/componentcontroller namenginx namespaceingress-nginx spec controllerk8s.io/ingress-nginx ---# Source: ingress-nginx/templates/admission-webhooks/validating-webhook.yaml# before changing this value, check the required kubernetes version# https://kubernetes.io/docs/reference/access-authn-authz/extensible-admission-controllers/#prerequisitesapiVersionadmissionregistration.k8s.io/v1 kindValidatingWebhookConfiguration metadata labels helm.sh/chartingress-nginx-4.0.10 app.kubernetes.io/nameingress-nginx app.kubernetes.io/instanceingress-nginx app.kubernetes.io/version1.1.0 app.kubernetes.io/managed-byHelm app.kubernetes.io/componentadmission-webhook nameingress-nginx-admission webhooksnamevalidate.nginx.ingress.kubernetes.io matchPolicyEquivalent rulesapiGroupsnetworking.k8s.io apiVersionsv1 operationsCREATE UPDATE resourcesingresses failurePolicyFail sideEffectsNone admissionReviewVersionsv1 clientConfig service namespaceingress-nginx nameingress-nginx-controller-admission path/networking/v1/ingresses ---# Source: ingress-nginx/templates/admission-webhooks/job-patch/serviceaccount.yamlapiVersionv1 kindServiceAccount metadata nameingress-nginx-admission namespaceingress-nginx annotations helm.sh/hookpre-install,pre-upgrade,post-install,post-upgrade helm.sh/hook-delete-policybefore-hook-creation,hook-succeeded labels helm.sh/chartingress-nginx-4.0.10 app.kubernetes.io/nameingress-nginx app.kubernetes.io/instanceingress-nginx app.kubernetes.io/version1.1.0 app.kubernetes.io/managed-byHelm app.kubernetes.io/componentadmission-webhook ---# Source: ingress-nginx/templates/admission-webhooks/job-patch/clusterrole.yamlapiVersionrbac.authorization.k8s.io/v1 kindClusterRole metadata nameingress-nginx-admission annotations helm.sh/hookpre-install,pre-upgrade,post-install,post-upgrade helm.sh/hook-delete-policybefore-hook-creation,hook-succeeded labels helm.sh/chartingress-nginx-4.0.10 app.kubernetes.io/nameingress-nginx app.kubernetes.io/instanceingress-nginx app.kubernetes.io/version1.1.0 app.kubernetes.io/managed-byHelm app.kubernetes.io/componentadmission-webhook rulesapiGroupsadmissionregistration.k8s.io resourcesvalidatingwebhookconfigurations verbsget update ---# Source: ingress-nginx/templates/admission-webhooks/job-patch/clusterrolebinding.yamlapiVersionrbac.authorization.k8s.io/v1 kindClusterRoleBinding metadata nameingress-nginx-admission annotations helm.sh/hookpre-install,pre-upgrade,post-install,post-upgrade helm.sh/hook-delete-policybefore-hook-creation,hook-succeeded labels helm.sh/chartingress-nginx-4.0.10 app.kubernetes.io/nameingress-nginx app.kubernetes.io/instanceingress-nginx app.kubernetes.io/version1.1.0 app.kubernetes.io/managed-byHelm app.kubernetes.io/componentadmission-webhook roleRef apiGrouprbac.authorization.k8s.io kindClusterRole nameingress-nginx-admission subjectskindServiceAccount nameingress-nginx-admission namespaceingress-nginx ---# Source: ingress-nginx/templates/admission-webhooks/job-patch/role.yamlapiVersionrbac.authorization.k8s.io/v1 kindRole metadata nameingress-nginx-admission namespaceingress-nginx annotations helm.sh/hookpre-install,pre-upgrade,post-install,post-upgrade helm.sh/hook-delete-policybefore-hook-creation,hook-succeeded labels helm.sh/chartingress-nginx-4.0.10 app.kubernetes.io/nameingress-nginx app.kubernetes.io/instanceingress-nginx app.kubernetes.io/version1.1.0 app.kubernetes.io/managed-byHelm app.kubernetes.io/componentadmission-webhook rulesapiGroups'' resourcessecrets verbsget create ---# Source: ingress-nginx/templates/admission-webhooks/job-patch/rolebinding.yamlapiVersionrbac.authorization.k8s.io/v1 kindRoleBinding metadata nameingress-nginx-admission namespaceingress-nginx annotations helm.sh/hookpre-install,pre-upgrade,post-install,post-upgrade helm.sh/hook-delete-policybefore-hook-creation,hook-succeeded labels helm.sh/chartingress-nginx-4.0.10 app.kubernetes.io/nameingress-nginx app.kubernetes.io/instanceingress-nginx app.kubernetes.io/version1.1.0 app.kubernetes.io/managed-byHelm app.kubernetes.io/componentadmission-webhook roleRef apiGrouprbac.authorization.k8s.io kindRole nameingress-nginx-admission subjectskindServiceAccount nameingress-nginx-admission namespaceingress-nginx ---# Source: ingress-nginx/templates/admission-webhooks/job-patch/job-createSecret.yamlapiVersionbatch/v1 kindJob metadata nameingress-nginx-admission-create namespaceingress-nginx annotations helm.sh/hookpre-install,pre-upgrade helm.sh/hook-delete-policybefore-hook-creation,hook-succeeded labels helm.sh/chartingress-nginx-4.0.10 app.kubernetes.io/nameingress-nginx app.kubernetes.io/instanceingress-nginx app.kubernetes.io/version1.1.0 app.kubernetes.io/managed-byHelm app.kubernetes.io/componentadmission-webhook spec template metadata nameingress-nginx-admission-create labels helm.sh/chartingress-nginx-4.0.10 app.kubernetes.io/nameingress-nginx app.kubernetes.io/instanceingress-nginx app.kubernetes.io/version1.1.0 app.kubernetes.io/managed-byHelm app.kubernetes.io/componentadmission-webhook spec containersnamecreate imagek8s.gcr.io/ingress-nginx/kube-webhook-certgenv1.1.1 imagePullPolicyIfNotPresent argscreate --host=ingress-nginx-controller-admission,ingress-nginx-controller-admission.$(POD_NAMESPACE).svc --namespace=$(POD_NAMESPACE) --secret-name=ingress-nginx-admission envnamePOD_NAMESPACE valueFrom fieldRef fieldPathmetadata.namespace securityContext allowPrivilegeEscalationfalse restartPolicyOnFailure serviceAccountNameingress-nginx-admission nodeSelector kubernetes.io/oslinux securityContext runAsNonRoottrue runAsUser2000---# Source: ingress-nginx/templates/admission-webhooks/job-patch/job-patchWebhook.yamlapiVersionbatch/v1 kindJob metadata nameingress-nginx-admission-patch namespaceingress-nginx annotations helm.sh/hookpost-install,post-upgrade helm.sh/hook-delete-policybefore-hook-creation,hook-succeeded labels helm.sh/chartingress-nginx-4.0.10 app.kubernetes.io/nameingress-nginx app.kubernetes.io/instanceingress-nginx app.kubernetes.io/version1.1.0 app.kubernetes.io/managed-byHelm app.kubernetes.io/componentadmission-webhook spec template metadata nameingress-nginx-admission-patch labels helm.sh/chartingress-nginx-4.0.10 app.kubernetes.io/nameingress-nginx app.kubernetes.io/instanceingress-nginx app.kubernetes.io/version1.1.0 app.kubernetes.io/managed-byHelm app.kubernetes.io/componentadmission-webhook spec containersnamepatch imagek8s.gcr.io/ingress-nginx/kube-webhook-certgenv1.1.1 imagePullPolicyIfNotPresent argspatch --webhook-name=ingress-nginx-admission --namespace=$(POD_NAMESPACE) --patch-mutating=false --secret-name=ingress-nginx-admission --patch-failure-policy=Fail envnamePOD_NAMESPACE valueFrom fieldRef fieldPathmetadata.namespace securityContext allowPrivilegeEscalationfalse restartPolicyOnFailure serviceAccountNameingress-nginx-admission nodeSelector kubernetes.io/oslinux securityContext runAsNonRoottrue runAsUser2000
创建ingress-nginx
kubectl apply -f deploy.yaml
成功之后
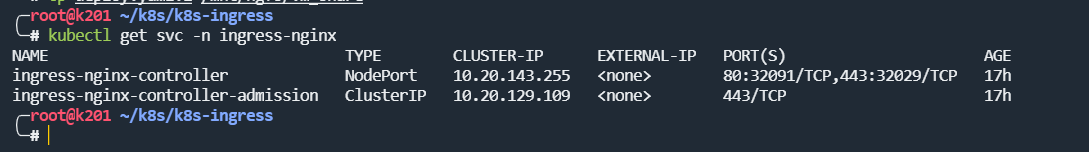
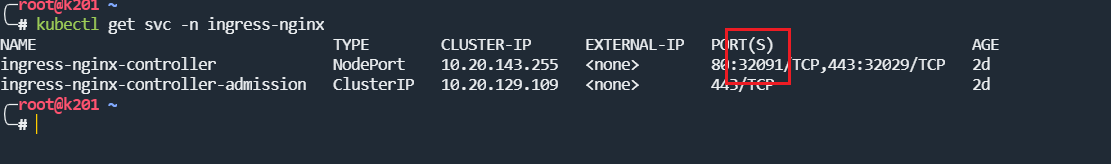
查看 ingress 相关service
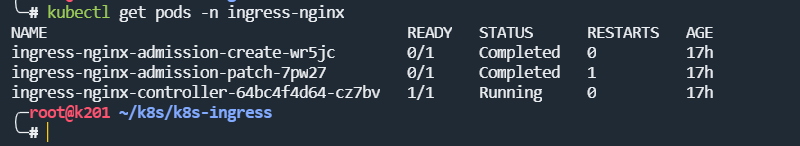
查看ingress 相关pod
确保以上启动成功
ingress 简单案例
创建deployment
test1_deployment.yaml
apiVersionapps/v1 kindDeployment metadata namedp-test-for-ingress spec replicas1 selector matchLabels apptest1 template metadata labels apptest1 spec containersimagenginx nametest portscontainerPort80 resources requests cpu1 limits cpu1---apiVersionv1 kindService metadata namesvc-test-for-ingress spec portsnamemyngx port2280 targetPort80 selector apptest1 typeNodePort
指定service的 type 类型为 NodePort
kubectl apply -f test1_deployment.yaml
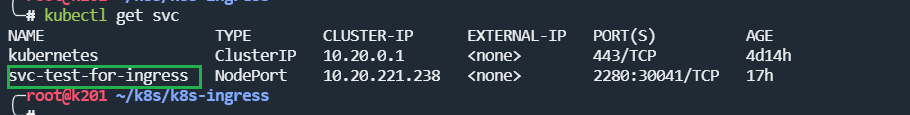
查看service
kubectl get svc
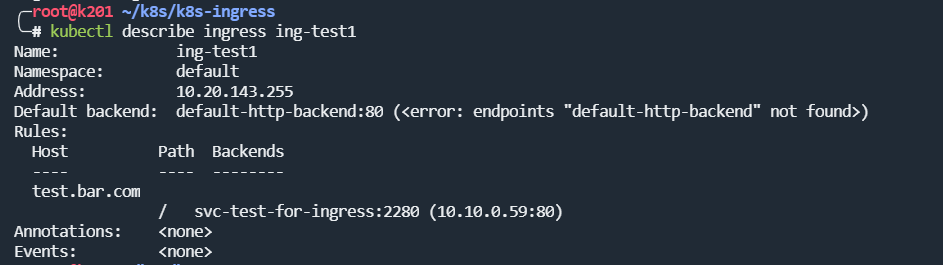
创建ingress
rule-test.yaml
apiVersionnetworking.k8s.io/v1 kindIngress metadata nameing-test1 spec ruleshosttest.bar.com http pathspathTypePrefix path"/" backend service namesvc-test-for-ingress port number2280 ingressClassNamenginx # 一定要指定ingressClassName
注意:
ingressClassName 一定要配置,如果不配置,创建的ingress的,无法找到class 和 无法分配Address
kubectl apply -f rule-test.yaml
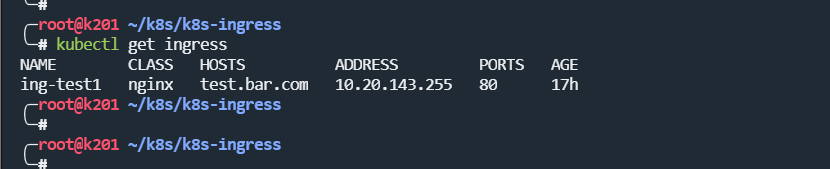
查看ingress
kubectl get ingress
外部访问
访问前需要配置
host 和 address 做映射
注意:
192.168.xx.xx:是宿主机的ip地址
test.bar.com:是ingress暴露的服务名,外部可以通过这个服务名访问
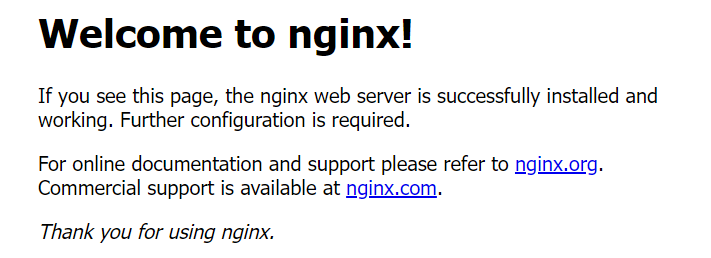
浏览器访问:
注意:
访问时,使用NodeIP : NodePort 方式访问。 而NodeIP就是在/etc/hosts文件中配置的宿主机上的IP地址
访问时,使用的是ingress-nginx-controller这个service的NodePort端口号,即为:32091
ingress 使用
基于名称的虚拟托管 -根据域名访问
基于名称的虚拟主机支持将针对多个主机名的 HTTP 流量路由到同一 IP 地址上
ingress 配置
apiVersionnetworking.k8s.io/v1 kindIngress metadata nametest spec ingressClassNameingress1 ruleshostfoo.bar.com http pathspathTypePrefix path"/" backend service nametest1 port number2180hostbar.foo.com http pathspathTypePrefix path"/" backend service nametest2 port number2280
如果你创建的 Ingress 资源没有在 rules 中定义的任何 hosts,则可以匹配指向 Ingress 控 制器 IP 地址的任何网络流量,而无需基于名称的虚拟主机。
简单扇出
一个扇出(fanout)配置根据请求的 HTTP URI 将来自同一 IP 地址的流量路由到多个 Service。 Ingress 允许你将负载均衡器的数量降至最低。例如,这样的设置:
ingress 配置
apiVersionnetworking.k8s.io/v1 kindIngress metadata nametest11 spec ingressClassNameingress1 ruleshosttest1.bar.com http pathspathTypePrefix path"/test1/" backend service nametest1 port number2180pathTypePrefix path"/test2/" backend service nametest1 port number2180
ingress 暴露多个服务
rules 和 paths 是数组,可以配置多个
ignress 配置
apiVersionnetworking.k8s.io/v1 kindIngress metadata nametest13 spec ingressClassNameingress1 ruleshosttest1.bar.com http pathspathTypePrefix path"/test1/" backend service nametest1 port number2180pathTypePrefix path"/test2/" backend service nametest1 port number2180hosttest3.bar.com http pathspathTypePrefix path"/" backend service nametest3 port number2380
ingress-限流
ingress配置
apiVersionnetworking.k8s.io/v1 kindIngress metadata annotations nginx.ingress.kubernetes.io/limit-rps"1" nameratelimit spec ruleshosttest1.bar.com http pathsbackend service nametest1 port number2180 path/ pathTypeExact
Ingress 处理 TLS 传输
证书准备
以上介绍的消息都是基于 Http 协议,Https 协议需要配置相关证书;客户端创建到 Ingress 控制器的 TLS 连接时,控制器将终止 TLS 连接; 客户端与 Ingress 控制器之间是加密的,而 Ingress 控制器和 pod 之间没有加密;要使控制 器可以这样,需要将证书和私钥附加到 Ingress 中;
通过设定包含 TLS 私钥和证书的 Secret 来保护 Ingress。 Ingress 只支持单个 TLS 端口 443,并假定 TLS 连接终止于 Ingress 节点 (与 Service 及其 Pod 之间的流量都以明 文传输)。 如果 Ingress 中的 TLS 配置部分指定了不同的主机,那么它们将根据通过 SNI TLS 扩展指定的主机名 (如果 Ingress 控制器支持 SNI)在同一端口上进行复用。 TLS Secret 必须包含名为 tls.crt 和 tls.key 的键名。 这些数据包含用于 TLS 的证书和私钥
生成key
openssl genrsa -out tls.key 2048
生成秘钥
将域名加入秘钥中
openssl req -new -x509 -key tls.key -out tls.cert -days 360 -subj /CN=test.bar.com
secret 创建
将生成的两个文件创建 secret
kubectl create secret tls tls-secret --cert=tls.cert --key=tls.key secret/tls-secret created
ingress创建
现在可以更新 Ingress 对象,以便它也接收 test.bar.com 的 HTTPS 请求
apiVersionnetworking.k8s.io/v1 kindIngress metadata nameing-test1 spec tls -hoststest.bar.com secretNametls-secret ruleshosttest.bar.com http pathspathTypePrefix path"/" backend service namesvc-test-for-ingress port number2280 ingressClassNamenginx
tls 中指定相关证书 在 Ingress 中引用此 Secret 将会告诉 Ingress 控制器使用 TLS 加密从客户端到负载均衡 器的通道。
你需要确保创建的 TLS Secret 创建自包含 test.bar.com 的公用名称 (CN)的证书。 这里的公共名称也被称为全限定域名(FQDN)。
ingress 高可用
Ingress 控制器启动引导时使用一些适用于所有 Ingress 的负载均衡策略设置, 例如负载 均衡算法、后端权重方案和其他等。 更高级的负载均衡概念(例如持久会话、动态权重) 尚未通过 Ingress 公开。 你可以通过用于服务的负载均衡器来获取这些功能。 值得注意的是,尽管健康检查不是通过 Ingress 直接暴露的,在 Kubernetes 中存在并行的 概念,比如 就绪检查, 允许你实现相同的目的。
修改 Nginx-controller 服务类型
kubectl edit svc -n ingress-nginx ingress-nginx-controller
kubectl get svc -n ingress-nginx ingress-nginx-controller NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE ingress-nginx-controller LoadBalancer 10.20.97.114 192.168.56.251 80:30493/TCP,443:30416/TCP 18h