下面测试的部署机ip地址为:192.168.10.205
1)yum安装OpenLDAP
|
1
|
[root@openldap-server ~]
# yum install openldap openldap-* -y
|
2)配置ldap,包括准备DB_CONFIG和slapd.conf
|
1
2
|
[root@openldap-server ~]
# cp /usr/share/openldap-servers/DB_CONFIG.example /var/lib/ldap/DB_CONFIG
[root@openldap-server ~]
# cp /usr/share/openldap-servers/slapd.conf.obsolete /etc/openldap/slapd.conf
|
3)生成ldap管理员密码
|
1
2
|
[root@openldap-server ~]
# slappasswd -s ldap@123
{SSHA}b6YpCvRFWAWQdJpueuyzk79VXlikj4Z1
|
4)修改slapd.conf,主要配置dc和rootpw,rootpw配置上面设置的密码(rootpw必须顶格写,与后面的密码用Tab键分开!可以把文件中rootpw前面的#去掉之后进行配置)
|
1
2
3
4
5
6
7
8
9
|
[root@openldap-server ~]
# cp /etc/openldap/slapd.conf /etc/openldap/slapd.conf.bak
[root@openldap-server ~]
# vim /etc/openldap/slapd.conf
......
database bdb
suffix
"dc=kevin,dc=com"
checkpoint 1024 15
rootdn
"cn=Manager,dc=kevin,dc=com"
#管理LDAP中信息的最高权限,即管理员权限
......
rootpw {SSHA}b6YpCvRFWAWQdJpueuyzk79VXlikj4Z1
|
5)检测并重新生成ldap数据库
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
|
[root@openldap-server ~]
# cd /etc/openldap/
[root@openldap-server openldap]
# ls slapd.d/
cn=config cn=config.ldif
[root@openldap-server openldap]
# rm -rf slapd.d/*
[root@openldap-server openldap]
# ls slapd.d/
[root@openldap-server openldap]
#
官方对于OpenLDAP2.4 ,不推荐使用 slapd.conf 作为配置文件。从这个版本开始所有配置数据都保存在
/etc/openldap/slapd
.d/中
[root@openldap-server openldap]
# rpm -qa|grep openldap
openldap-2.4.40-16.el6.x86_64
openldap-servers-sql-2.4.40-16.el6.x86_64
openldap-devel-2.4.40-16.el6.x86_64
openldap-servers-2.4.40-16.el6.x86_64
openldap-clients-2.4.40-16.el6.x86_64
[root@openldap-server openldap]
# slaptest -f /etc/openldap/slapd.conf -F /etc/openldap/slapd.d/
5b02d207 bdb_db_open: database
"dc=kevin,dc=com"
: db_open(
/var/lib/ldap/id2entry
.bdb) failed: No such
file
or directory (2).
5b02d207 backend_startup_one (
type
=bdb, suffix=
"dc=kevin,dc=com"
): bi_db_open failed! (2)
slap_startup failed (
test
would succeed using the -u switch)
[root@openldap-server openldap]
# slaptest -u
config
file
testing succeeded
|
6)修改相关ldap文件权限
|
1
2
|
[root@openldap-server openldap]
# chown -R ldap:ldap /var/lib/ldap/
[root@openldap-server openldap]
# chown -R ldap:ldap /etc/openldap/
|
7)启动slapd服务
|
1
2
3
4
5
6
7
8
|
[root@openldap-server openldap]
# service slapd start
Starting slapd: [ OK ]
[root@openldap-server openldap]
# service slapd status
slapd (pid 12896) is running...
[root@openldap-server openldap]
# lsof -i:389
COMMAND PID USER FD TYPE DEVICE SIZE
/OFF
NODE NAME
slapd 12896 ldap 7u IPv4 702934 0t0 TCP *:ldap (LISTEN)
slapd 12896 ldap 8u IPv6 702935 0t0 TCP *:ldap (LISTEN)
|
8)yum安装migrationtools
|
1
|
[root@openldap-server openldap]
# yum install migrationtools -y
|
9)编辑/usr/share/migrationtools/migrate_common.ph并修改相关配置
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
|
[root@openldap-server openldap]
# cp /usr/share/migrationtools/migrate_common.ph /usr/share/migrationtools/migrate_common.ph.bak
[root@openldap-server openldap]
# vim /usr/share/migrationtools/migrate_common.ph
......
# Default DNS domain
$DEFAULT_MAIL_DOMAIN =
"kevin.com"
;
# Default base
$DEFAULT_BASE =
"dc=kevin,dc=com"
;
[root@openldap-server openldap]
# diff /usr/share/migrationtools/migrate_common.ph /usr/share/migrationtools/migrate_common.ph.bak
71c71
< $DEFAULT_MAIL_DOMAIN =
"kevin.com"
;
---
> $DEFAULT_MAIL_DOMAIN =
"padl.com"
;
74c74
< $DEFAULT_BASE =
"dc=kevin,dc=com"
;
---
> $DEFAULT_BASE =
"dc=padl,dc=com"
;
|
10)生成base.ldif
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
|
[root@openldap-server openldap]
# /usr/share/migrationtools/migrate_base.pl >base.ldif
[root@openldap-server openldap]
# cat base.ldif
dn:
dc
=kevin,
dc
=com
dc
: kevin
objectClass:
top
objectClass: domain
dn: ou=Hosts,
dc
=kevin,
dc
=com
ou: Hosts
objectClass:
top
objectClass: organizationalUnit
dn: ou=Rpc,
dc
=kevin,
dc
=com
ou: Rpc
objectClass:
top
objectClass: organizationalUnit
dn: ou=Services,
dc
=kevin,
dc
=com
ou: Services
objectClass:
top
objectClass: organizationalUnit
dn: nisMapName=netgroup.byuser,
dc
=kevin,
dc
=com
nismapname: netgroup.byuser
objectClass:
top
objectClass: nisMap
dn: ou=Mounts,
dc
=kevin,
dc
=com
ou: Mounts
objectClass:
top
objectClass: organizationalUnit
dn: ou=Networks,
dc
=kevin,
dc
=com
ou: Networks
objectClass:
top
objectClass: organizationalUnit
dn: ou=People,
dc
=kevin,
dc
=com
ou: People
objectClass:
top
objectClass: organizationalUnit
dn: ou=Group,
dc
=kevin,
dc
=com
ou: Group
objectClass:
top
objectClass: organizationalUnit
dn: ou=Netgroup,
dc
=kevin,
dc
=com
ou: Netgroup
objectClass:
top
objectClass: organizationalUnit
dn: ou=Protocols,
dc
=kevin,
dc
=com
ou: Protocols
objectClass:
top
objectClass: organizationalUnit
dn: ou=Aliases,
dc
=kevin,
dc
=com
ou: Aliases
objectClass:
top
objectClass: organizationalUnit
dn: nisMapName=netgroup.byhost,
dc
=kevin,
dc
=com
nismapname: netgroup.byhost
objectClass:
top
objectClass: nisMap
|
11)添加base.ldif到ldap(输入密码为上面创建的:ldap@123)
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
|
[root@openldap-server openldap]
# ldapadd -x -D "cn=Manager,dc=kevin,dc=com" -W -f ./base.ldif
Enter LDAP Password:
adding new entry
"dc=kevin,dc=com"
adding new entry
"ou=Hosts,dc=kevin,dc=com"
adding new entry
"ou=Rpc,dc=kevin,dc=com"
adding new entry
"ou=Services,dc=kevin,dc=com"
adding new entry
"nisMapName=netgroup.byuser,dc=kevin,dc=com"
adding new entry
"ou=Mounts,dc=kevin,dc=com"
adding new entry
"ou=Networks,dc=kevin,dc=com"
adding new entry
"ou=People,dc=kevin,dc=com"
adding new entry
"ou=Group,dc=kevin,dc=com"
adding new entry
"ou=Netgroup,dc=kevin,dc=com"
adding new entry
"ou=Protocols,dc=kevin,dc=com"
adding new entry
"ou=Aliases,dc=kevin,dc=com"
adding new entry
"nisMapName=netgroup.byhost,dc=kevin,dc=com"
|
12)检查ldapadd是否成功(输入密码为上面创建的:ldap@123)(必须检查确认Manager数据添加了,才能通过phpldapAdmin登录)
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
|
[root@openldap-server openldap]
# ldapsearch -x -D "cn=Manager,dc=kevin,dc=com" -b "ou=Aliases,dc=kevin,dc=com" -W
Enter LDAP Password:
# extended LDIF
#
# LDAPv3
# base <ou=Aliases,dc=kevin,dc=com> with scope subtree
# filter: (objectclass=*)
# requesting: ALL
#
# Aliases, kevin.com
dn: ou=Aliases,
dc
=kevin,
dc
=com
ou: Aliases
objectClass:
top
objectClass: organizationalUnit
# search result
search: 2
result: 0 Success
# numResponses: 2
# numEntries: 1
|
13)yum安装httpd及PhpLdapAdmin
|
1
2
|
[root@openldap-server openldap]
# rpm -ivh http://mirrors.ukfast.co.uk/sites/dl.fedoraproject.org/pub/epel/6/x86_64/epel-release-6-8.noarch.rpm
[root@openldap-server openldap]
# yum install httpd phpldapadmin -y
|
14)配置/etc/httpd/conf.d/phpldapadmin.conf允许从远程访问
|
1
2
3
4
5
6
7
8
9
10
11
|
[root@openldap-server openldap]
# vim /etc/httpd/conf.d/phpldapadmin.conf #可以先把此文件cp备份一份
Alias
/phpldapadmin
/usr/share/phpldapadmin/htdocs
Alias
/ldapadmin
/usr/share/phpldapadmin/htdocs
<Directory
/usr/share/phpldapadmin/htdocs
>
Order Deny,Allow
Allow from all
Allow from 127.0.0.1
#或者去掉下面这三行内容,表示运行所有客户机访问(本测试案例就去掉了这三行)
Allow from ::1
Allow from 192.168.10.206 192.168.10.207
#允许哪些IP地址访问phpldapadmin
<
/Directory
>
|
15)修改/etc/phpldapadmin/config.php配置用DN登录
|
1
2
3
4
5
6
7
8
9
10
11
12
13
|
[root@openldap-server openldap]
# cp /etc/phpldapadmin/config.php /etc/phpldapadmin/config.php.bak
[root@openldap-server openldap]
# vim /etc/phpldapadmin/config.php
.......
//
$servers->setValue(
'login'
,
'attr'
,
'uid'
);
#注释掉这一行
$servers->setValue(
'login'
,
'attr'
,
'dn'
);
#添加这一行
[root@openldap-server openldap]
# diff /etc/phpldapadmin/config.php /etc/phpldapadmin/config.php.bak
398,399c398,399
<
//
$servers->setValue(
'login'
,
'attr'
,
'uid'
);
< $servers->setValue(
'login'
,
'attr'
,
'dn'
);
---
> $servers->setValue(
'login'
,
'attr'
,
'uid'
);
>
|
16)启动httpd服务
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
|
[root@openldap-server openldap]
# service httpd start
Starting httpd: httpd: apr_sockaddr_info_get() failed
for
openldap-server
httpd: Could not reliably determine the server's fully qualified domain name, using 127.0.0.1
for
ServerName
[ OK ]
[root@openldap-server openldap]
# service httpd status
httpd (pid 13010) is running...
[root@openldap-server openldap]
# lsof -i:80
COMMAND PID USER FD TYPE DEVICE SIZE
/OFF
NODE NAME
httpd 13010 root 4u IPv6 757231 0t0 TCP *:http (LISTEN)
httpd 13012 apache 4u IPv6 757231 0t0 TCP *:http (LISTEN)
httpd 13013 apache 4u IPv6 757231 0t0 TCP *:http (LISTEN)
httpd 13014 apache 4u IPv6 757231 0t0 TCP *:http (LISTEN)
httpd 13015 apache 4u IPv6 757231 0t0 TCP *:http (LISTEN)
httpd 13016 apache 4u IPv6 757231 0t0 TCP *:http (LISTEN)
httpd 13017 apache 4u IPv6 757231 0t0 TCP *:http (LISTEN)
httpd 13018 apache 4u IPv6 757231 0t0 TCP *:http (LISTEN)
httpd 13019 apache 4u IPv6 757231 0t0 TCP *:http (LISTEN)
|
17)打开Web UI并登录LDAP(登录用户名为"cn=Manager,dc=kevin,dc=com",密码为"ldap@123")


18)导入新数据
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
|
[root@openldap-server openldap]
# pwd
/etc/openldap
[root@openldap-server openldap]
# vim test.ldif
dn: ou=technology,
dc
=kevin,
dc
=com
changetype: add
objectclass:
top
objectclass: organizationalUnit
ou: technology
dn: cn=wang shibo,ou=technology,
dc
=kevin,
dc
=com
changetype: add
objectclass: person
objectclass: organizationalPerson
objectclass: inetOrgPerson
cn: wang shibo
sn: wang
ou: technology
description: boy,
man
description:
man
uid: goodman
[root@openldap-server openldap]
# ldapadd -x -D "cn=Manager,dc=kevin,dc=com" -w ldap@123 -f test.ldif
adding new entry
"ou=technology,dc=kevin,dc=com"
adding new entry
"cn=wang shibo,ou=technology,dc=kevin,dc=com"
============================================================
如果报错:
[root@openldap-server openldap]
# ldapadd -x -D "cn=Manager,dc=kevin,dc=com" -w ldap@123 -f test.ldif
ldapadd: attributeDescription
"dn"
: (possible missing newline after line 9, entry
"ou=technology,dc=kevin,dc=com"
?)
adding new entry
"ou=technology,dc=kevin,dc=com"
ldap_add: Type or value exists (20)
additional info: ou: value
#0 provided more than once
产生原因:
test
.ldif文件中的不规范的空格所致!!即导入的数据含有空格所致!
纠错如下:
dn:(空格)ou=technology,
dc
=kevin,
dc
=com
changetype:(空格)add(结尾无空格)
objectclass:(空格)
top
(结尾无空格)
objectclass:(空格)organizationalUnit(结尾无空格)
ou:(空格)echnology(结尾无空格)
(1空行,空行必须要定格,不能留空格)(结尾无空格)
........(后面的配置内容纠正方法同样)
===========================================================
查看上面所导入的数据:
[root@openldap-server openldap]
# ldapsearch -x -D "cn=Manager,dc=kevin,dc=com" -b "ou=technology,dc=kevin,dc=com" -w ldap@123
# extended LDIF
#
# LDAPv3
# base <ou=technology,dc=kevin,dc=com> with scope subtree
# filter: (objectclass=*)
# requesting: ALL
#
# technology, kevin.com
dn: ou=technology,
dc
=kevin,
dc
=com
objectClass:
top
objectClass: organizationalUnit
ou: technology
# wang shibo, technology, kevin.com
dn: cn=wang shibo,ou=technology,
dc
=kevin,
dc
=com
objectClass: person
objectClass: organizationalPerson
objectClass: inetOrgPerson
cn: wang shibo
sn: wang
ou: technology
description: boy,
man
description:
man
uid: goodman
# search result
search: 2
result: 0 Success
# numResponses: 3
# numEntries: 2
|
可以登陆phpLDAPadmin的web界面查询新导入的数据
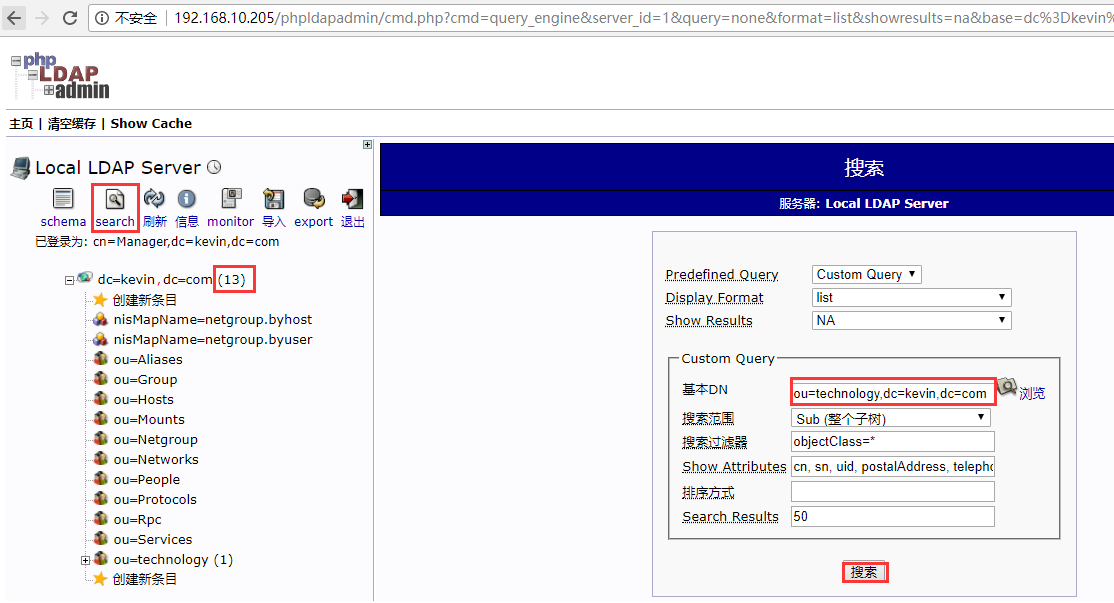
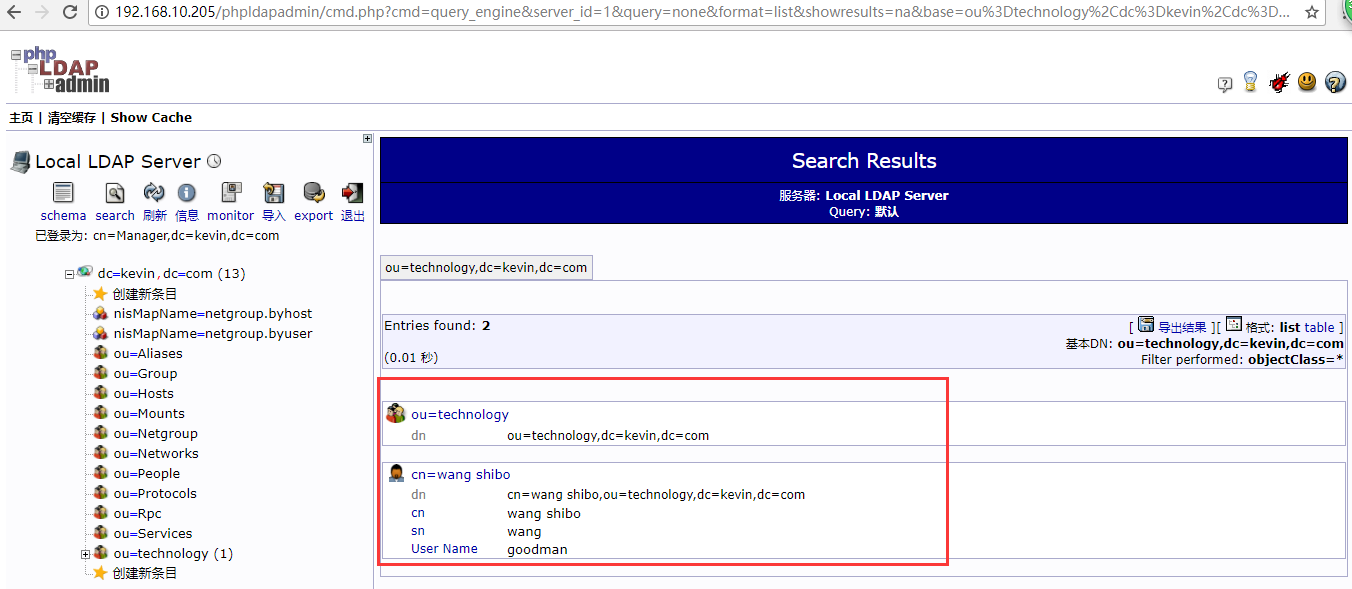
再次导入其他数据
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
|
[root@openldap-server openldap]
# vim test.ldif
dn: cn=chenlu,ou=technology,
dc
=kevin,
dc
=com
changetype: add
objectclass: person
objectclass: organizationalPerson
objectclass: inetOrgPerson
cn: chenlu
sn: chenlu
ou: technology
description: girl
uid: UI Designer
[root@openldap-server openldap]
# ldapadd -x -D "cn=Manager,dc=kevin,dc=com" -w ldap@123 -f test.ldif
adding new entry
"cn=chenlu,ou=technology,dc=kevin,dc=com"
[root@openldap-server openldap]
# ldapsearch -x -D "cn=Manager,dc=kevin,dc=com" -b "ou=technology,dc=kevin,dc=com" -w ldap@123
# extended LDIF
#
# LDAPv3
# base <ou=technology,dc=kevin,dc=com> with scope subtree
# filter: (objectclass=*)
# requesting: ALL
#
# technology, kevin.com
dn: ou=technology,
dc
=kevin,
dc
=com
objectClass:
top
objectClass: organizationalUnit
ou: technology
# wang shibo, technology, kevin.com
dn: cn=wang shibo,ou=technology,
dc
=kevin,
dc
=com
objectClass: person
objectClass: organizationalPerson
objectClass: inetOrgPerson
cn: wang shibo
sn: wang
ou: technology
description: boy,
man
description:
man
uid: goodman
# chenlu, technology, kevin.com
dn: cn=chenlu,ou=technology,
dc
=kevin,
dc
=com
objectClass: person
objectClass: organizationalPerson
objectClass: inetOrgPerson
cn: chenlu
sn: chenlu
ou: technology
description: girl
uid: UI Designer
# search result
search: 2
result: 0 Success
# numResponses: 4
# numEntries: 3
|

===============OpenLDAP日志功能开启=================
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
|
1)需要在slapd.conf配置文件里加上日志行 ,这里的日志级别有很多种,这里选择256这个值的级别(主从节点都要打开openldap日志功能)
[root@openldap-master ~]
# cp /etc/openldap/slapd.conf /etc/openldap/slapd.conf.bak3
[root@openldap-master ~]
# vim /etc/openldap/slapd.conf #中间的空格用tab键分开
.......
loglevel 256
2)修改了配置文件,所有得重新生成配置文件的信息
[root@openldap-master ~]
# rm -rf /etc/openldap/slapd.d/*
[root@openldap-master ~]
# slaptest -f /etc/openldap/slapd.conf -F /etc/openldap/slapd.d/
config
file
testing succeeded
[root@openldap-master ~]
# slaptest -u
config
file
testing succeeded
[root@openldap-master ~]
# chown -R ldap:ldap /var/lib/ldap/
[root@openldap-master ~]
# chown -R ldap:ldap /etc/openldap/
3)修改
/etc/rsyslog
.conf文件,加上下面内容
[root@openldap-master ~]
# cp /etc/rsyslog.conf /etc/rsyslog.conf.bak
[root@openldap-master ~]
# vim /etc/rsyslog.conf
........
local4.*
/var/log/slapd/slapd
.log
4)创建日志文件目录,授权
[root@openldap-master ~]
# mkdir /var/log/slapd
[root@openldap-master ~]
# chmod 755 /var/log/slapd/
[root@openldap-master ~]
# chown ldap.ldap /var/log/slapd/
5)重启syslog服务和slapd服务
[root@openldap-master ~]
# /etc/init.d/rsyslog restart
Shutting down system logger: [ OK ]
Starting system logger: [ OK ]
[root@openldap-master ~]
# /etc/init.d/slapd restart
Stopping slapd: [ OK ]
Starting slapd: [ OK ]
[root@openldap-master ~]
# lsof -i:389
COMMAND PID USER FD TYPE DEVICE SIZE
/OFF
NODE NAME
slapd 13773 ldap 7u IPv4 840484 0t0 TCP *:ldap (LISTEN)
slapd 13773 ldap 8u IPv6 840485 0t0 TCP *:ldap (LISTEN)
6)查看openldap日志信息
[root@openldap-master ~]
# tail -f /var/log/slapd/slapd.log
|
===============OpenLDAP主从模式配置=================
OpenLDAP主从同步的原理:当在主服务器上更新数据时,该更新通过更新日志记录,并将更新复制到从服务器上
OpenLdap v2.3之前的同步复制缺点
- slurpd守护进程是以推模式操作 : 主服务器推送变更的数据到从服务器 (不可靠)
- 对replog中的记录的次序极为敏感
- 很容易失去同步, 这时需要手工干预来从主目录重新同步从服务器数据库
- 如果一个从服务器长时间停机,replog可能变得太大以至于slurpd无法处理
- 只工作在推模式(也可以设置为拉模式,但是这种感觉类似于将master上的数据做了一个快捷连接到slave上)
- 需要停止和重新启动主服务器来增加从服务器
- 只支持单一主服务器复制(1台主对多从)
OpenLDAP v2.4之后的同步功能
新版最大的功能就是实现了双向复制,即双主、多主模式,无论哪一台master宕机,都不会影响使用。
新版主从配置有五种方式:
1)Syncrepl
该方式是slave服务器以拉的方式同步master的用户数据,这是基本也是最简单的openldap主从配置的方式。
该方式缺点:当修改一个条目中的一个属性值(or大批量的万级别的某1属性值),它不是简单的同步过来这些属性,而是把修改的条目一起同步更新来。
2)Delta-syncrepl
比上一条多了个功能:基于日志同步:
在master每更改1条记录,肯定会产生1条日志,那么slave会通过你的master日志进行相应的修改,这就克服了上一条的缺点。
3)N-Way Multi-Master
多主方式同步LDAP信息
4)MirrorMode
该方式是服务器互相推送信息的方式同步用户数据;MirrorMode只支持2个主master(2个主master可以+N个slave),但是你如果非得加了3 、4 台master后,
那么其余的都只能从前2台master上获取数据,而不能将本身的数据推送过去。如果你有类似需求,也可以使用这个方式。(比如,你企业分散点多,然后不希望
都具有修改功能,可以使用它)
5)Syncrepl Proxy
代理同步。意思是将主master隐藏起来,而代理机上边通过Syncrepl从master主机以拉的方式同步master用户数据,当代理主机发生改变时,代理主机的LDAP
又以推的方式将数据更新到下属的slave LDAP服务器上。slave LDAP 只有对代理LDAP服务器的读权限。
Syncrepl同步解释
由于syncrepl为拉取模式(到master拉数据),所以配置文件配置slave端的slapd.conf文件即可。初始化操作2种:
1)通过配置文件,当开启syncrepl引擎后会到master拉数据;
2)从主服务器备份数据,复制到slave。当从备份数据初始化的时候,不必担心数据老,因为syncrepl会自动进行校验,然后进行相应的修改、同步。
(当复制一个大规模的“条录”,建议从备份初始化)
需要注意的是:slave是使用读写权限到master中进行同步的!
基于上面的部署,上面的测试机192.168.10.205作为openldap-master主节点,新增一台服务器192.168.10.206作为openldap-slave从节点。OpenLDAP主从配置如下:
1)基础环境
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
|
192.168.10.205 openldap-master
192.168.10.206 openldap-slave
绑定hosts(两个节点机器上都要操作)
[root@openldap-master ~]
# cat /etc/hosts
......
192.168.10.205 openldap-master
192.168.10.206 openldap-slave
关闭两个节点机器的防火墙和selinux(两个节点机器上都要操作)
[root@openldap-master ~]
# /etc/init.d/iptables stop
[root@openldap-master ~]
# chkconfig iptables off
[root@openldap-master ~]
# chkconfig --list|grep iptables
iptables 0:off 1:off 2:off 3:off 4:off 5:off 6:off
同步系统时间(两个节点机器上都要操作)
[root@openldap-master ~]
# yum install -y ntpdate
[root@openldap-master ~]
# ntpdate ntp1.aliyun.com
|
2)openldap-slave从节点同样安装和配置OpenLDAP和PhpLdapAdmin(和上面安装即配置步骤一样,在此省略)。为了测试效果,设置从节点的密码为123@ldap
|
1
2
|
[root@openldap-slave ~]
# slappasswd -s 123@ldap
{SSHA}X3wlj1uJmB50FM4rNN4869VCeMd92Pcr
|
3)penldap-master主节点和openldap-slave从节点的PhpLdapAdmin和http配置一样
4)OpenLDAP的主从配置
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
|
-----------------------------------------------------------------
penldap-master主节点的配置如下:
[root@openldap-master ~]
# cp /etc/openldap/slapd.conf /etc/openldap/slapd.conf.bak2
[root@openldap-master ~]
# vim /etc/openldap/slapd.conf #在文件底部添加下面同步配置(之前的配置不动)
......
modulepath
/usr/lib/openldap
#一定要打开这几行的注释
modulepath
/usr/lib64/openldap
......
moduleload syncprov.la
......
#replication
index entryCSN,entryUUID
eq
overlay syncprov
syncprov-nopresent TRUE
syncprov-reloadhint TRUE
syncprov-checkpoint 100 10
syncprov-sessionlog 100
重新生成主节点的配置文件
[root@openldap-master ~]
# rm -rf /etc/openldap/slapd.d/*
[root@openldap-master ~]
# slaptest -f /etc/openldap/slapd.conf -F /etc/openldap/slapd.d/
config
file
testing succeeded
[root@openldap-master ~]
# slaptest -u
config
file
testing succeeded
[root@openldap-master ~]
# chown -R ldap:ldap /var/lib/ldap/
[root@openldap-master ~]
# chown -R ldap:ldap /etc/openldap/
[root@openldap-master ~]
# service slapd restart
Stopping slapd: [ OK ]
Starting slapd: [ OK ]
[root@openldap-master ~]
# lsof -i:389
COMMAND PID USER FD TYPE DEVICE SIZE
/OFF
NODE NAME
slapd 13214 ldap 7u IPv4 763380 0t0 TCP *:ldap (LISTEN)
slapd 13214 ldap 8u IPv6 763381 0t0 TCP *:ldap (LISTEN)
----------------------------------------------------------------
penldap-slave从节点的配置如下:
[root@openldap-slave ~]
# cp /etc/openldap/slapd.conf /etc/openldap/slapd.conf.bak2
[root@openldap-slave ~]
# vim /etc/openldap/slapd.conf
......
modulepath
/usr/lib/openldap
#一定要打开这几行的注释
modulepath
/usr/lib64/openldap
......
moduleload syncprov.la
......
database bdb
suffix
"dc=kevin,dc=com"
checkpoint 1024 15
rootdn
"cn=Manager,dc=kevin,dc=com"
.......
rootpw {SSHA}X3wlj1uJmB50FM4rNN4869VCeMd92Pcr
.......
# slave replica statement start
syncrepl rid=123
provider=ldap:
//192
.168.10.205:389
type
=refreshOnly
interval=00:00:00:01
searchbase=
"dc=kevin,dc=com"
scope=sub
attrs=
"*"
schemachecking=off
bindmethod=simple
binddn=
"cn=Manager,dc=kevin,dc=com"
credentials=ldap@123
重新生成从节点的配置文件
[root@openldap-slave ~]
# rm -rf /etc/openldap/slapd.d/*
[root@openldap-slave ~]
# slaptest -f /etc/openldap/slapd.conf -F /etc/openldap/slapd.d/
5b02f6ae syncrepl rid=123 searchbase=
"dc=kevin,dc=com"
: no retry defined, using default
config
file
testing succeeded
[root@openldap-slave ~]
# slaptest -u
5b02f6b4 syncrepl rid=123 searchbase=
"dc=kevin,dc=com"
: no retry defined, using default
config
file
testing succeeded
[root@openldap-slave ~]
# chown -R ldap:ldap /var/lib/ldap/
[root@openldap-slave ~]
# chown -R ldap:ldap /etc/openldap/
[root@openldap-slave ~]
# service slapd restart
Stopping slapd: [ OK ]
Checking configuration files
for
slapd: [WARNING]
5b02f6c6 syncrepl rid=123 searchbase=
"dc=kevin,dc=com"
: no retry defined, using default
config
file
testing succeeded
Starting slapd: [ OK ]
[root@openldap-slave ~]
# lsof -i:389
COMMAND PID USER FD TYPE DEVICE SIZE
/OFF
NODE NAME
slapd 14329 ldap 7u IPv4 4803594 0t0 TCP *:ldap (LISTEN)
slapd 14329 ldap 8u IPv6 4803595 0t0 TCP *:ldap (LISTEN)
|
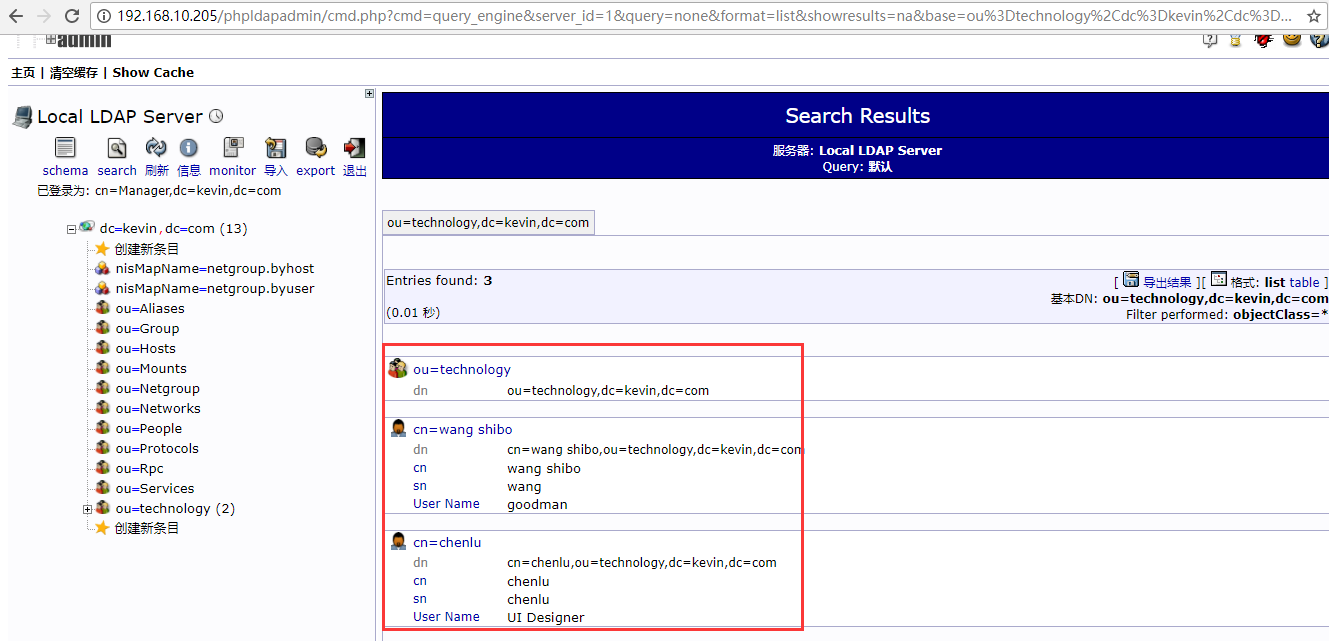
5)登陆openldap-slave从节点的phpLDAPadmin的web界面(http://192.168.10.206/phpldapadmin),发现已经将上面openldap-master主节点新导入的数据同步过来了
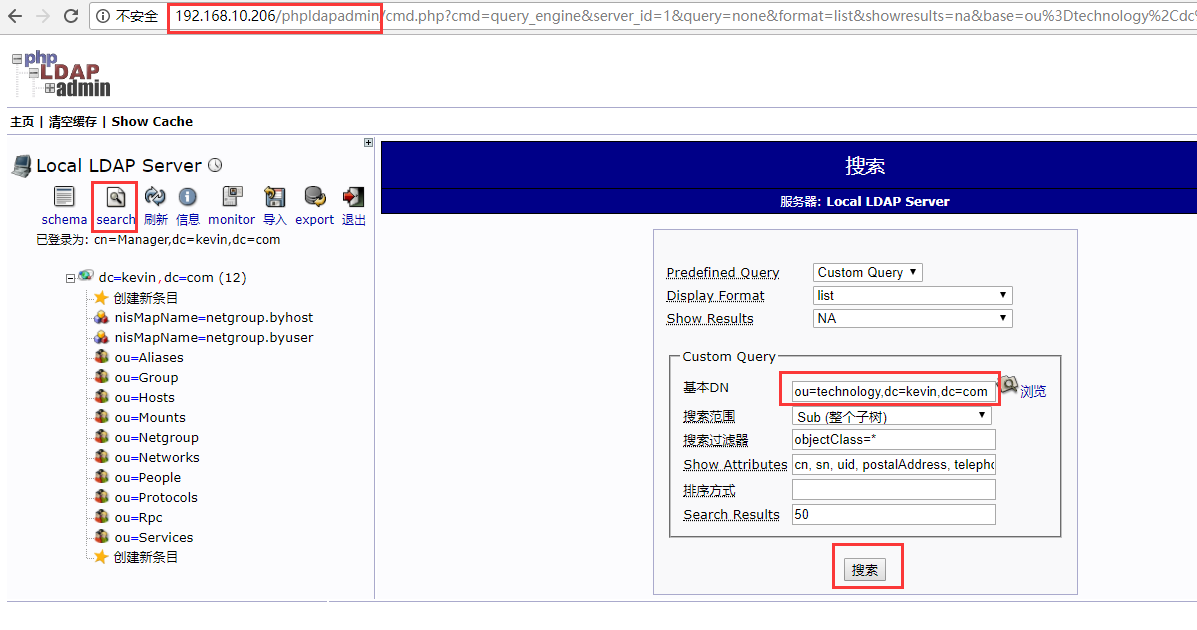
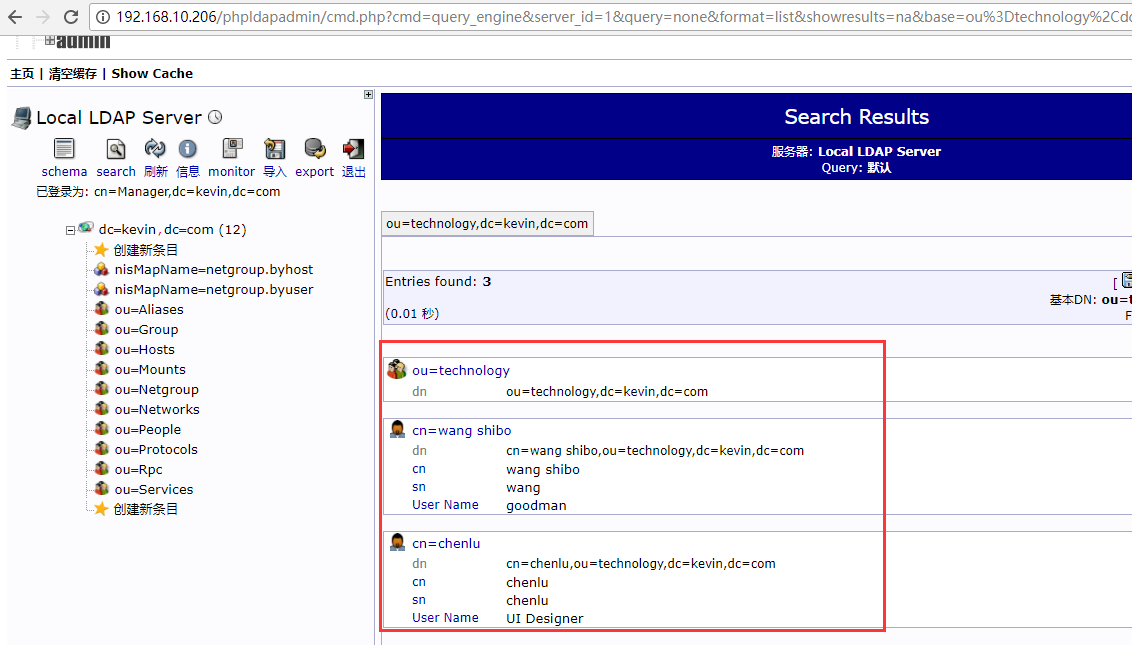
6)导入新数据测试主从同步效果
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
170
171
172
173
174
175
176
177
178
179
180
181
182
183
184
185
186
187
188
189
190
191
192
193
194
195
196
197
198
199
200
201
202
203
204
205
206
207
208
209
210
211
212
213
214
215
216
217
218
219
|
温馨提示:由于在syncrepl中slave是refreshOnly,相当于从节点是只读的,这时不允许在从节点导入或者删除用户,否则会出现错误!
因为只能在master主节点上导入数据:
前面已经编辑了base.ldif,并导入了该文件中定义的数据了(即
dc
=kevin,
dc
=com、ou=People,
dc
=kevin,
dc
=com、ou=Group,
dc
=kevin,
dc
=com等)
[root@openldap-master openldap]
# pwd
/etc/openldap
[root@openldap-master openldap]
# cat group.ldif
dn: cn=user1,ou=Group,
dc
=kevin,
dc
=com
objectClass: posixGroup
objectClass:
top
cn: user1
userPassword: kevin123
gidNumber: 10011
dn: cn=user2,ou=Group,
dc
=kevin,
dc
=com
objectClass: posixGroup
objectClass:
top
cn: user2
userPassword: kevin123
gidNumber: 10012
dn: cn=user3,ou=Group,
dc
=kevin,
dc
=com
objectClass: posixGroup
objectClass:
top
cn: user3
userPassword: kevin123
gidNumber: 10013
[root@openldap-master openldap]
# cat people.ldif
dn: uid=user1,ou=People,
dc
=kevin,
dc
=com
uid: user1
cn: user1
objectClass: account
objectClass: posixAccount
objectClass:
top
objectClass: shadowAccount
userPassword: kevin123
shadowLastChange: 17053
shadowMin: 0
shadowMax: 99999
shadowWarning: 7
loginShell:
/bin/bash
uidNumber: 10011
gidNumber: 10011
homeDirectory:
/home/user1
dn: uid=user2,ou=People,
dc
=kevin,
dc
=com
uid: user2
cn: user2
objectClass: account
objectClass: posixAccount
objectClass:
top
objectClass: shadowAccount
userPassword: kevin123
shadowLastChange: 17053
shadowMin: 0
shadowMax: 99999
shadowWarning: 7
loginShell:
/bin/bash
uidNumber: 10012
gidNumber: 10012
homeDirectory:
/home/user2
dn: uid=user3,ou=People,
dc
=kevin,
dc
=com
uid: user3
cn: user3
objectClass: account
objectClass: posixAccount
objectClass:
top
objectClass: shadowAccount
userPassword: kevin123
shadowLastChange: 17053
shadowMin: 0
shadowMax: 99999
shadowWarning: 7
loginShell:
/bin/bash
uidNumber: 10013
gidNumber: 10013
homeDirectory:
/home/user3
执行数据导入
[root@openldap-master openldap]
# ldapadd -x -D "cn=Manager,dc=kevin,dc=com" -w ldap@123 -f group.ldif
adding new entry
"cn=user1,ou=Group,dc=kevin,dc=com"
adding new entry
"cn=user2,ou=Group,dc=kevin,dc=com"
adding new entry
"cn=user3,ou=Group,dc=kevin,dc=com"
[root@openldap-master openldap]
# ldapadd -x -D "cn=Manager,dc=kevin,dc=com" -w ldap@123 -f people.ldif
adding new entry
"uid=user1,ou=People,dc=kevin,dc=com"
adding new entry
"uid=user2,ou=People,dc=kevin,dc=com"
adding new entry
"uid=user3,ou=People,dc=kevin,dc=com"
openldap-master主节点查看
[root@openldap-master openldap]
# ldapsearch -x -D "cn=Manager,dc=kevin,dc=com" -b "ou=Group,dc=kevin,dc=com" -w ldap@123
[root@openldap-master openldap]
# ldapsearch -x -D "cn=Manager,dc=kevin,dc=com" -b "ou=People,dc=kevin,dc=com" -w ldap@123
现在在openldap-slave从节点上查看(注意这里的从节点设置的ldap密码是123@ldap,和主节点的ldap密码不一样):
[root@openldap-slave ldap]
# ldapsearch -x -D "cn=Manager,dc=kevin,dc=com" -b "ou=People,dc=kevin,dc=com" -w 123@ldap
# extended LDIF
#
# LDAPv3
# base <ou=People,dc=kevin,dc=com> with scope subtree
# filter: (objectclass=*)
# requesting: ALL
#
# People, kevin.com
dn: ou=People,
dc
=kevin,
dc
=com
ou: People
objectClass:
top
objectClass: organizationalUnit
# user1, People, kevin.com
dn: uid=user1,ou=People,
dc
=kevin,
dc
=com
uid: user1
cn: user1
objectClass: account
objectClass: posixAccount
objectClass:
top
objectClass: shadowAccount
userPassword:: a2V2aW4xMjM=
shadowLastChange: 17053
shadowMin: 0
shadowMax: 99999
shadowWarning: 7
loginShell:
/bin/bash
uidNumber: 10011
gidNumber: 10011
homeDirectory:
/home/user1
# user2, People, kevin.com
dn: uid=user2,ou=People,
dc
=kevin,
dc
=com
uid: user2
cn: user2
objectClass: account
objectClass: posixAccount
objectClass:
top
objectClass: shadowAccount
userPassword:: a2V2aW4xMjM=
shadowLastChange: 17053
shadowMin: 0
shadowMax: 99999
shadowWarning: 7
loginShell:
/bin/bash
uidNumber: 10012
gidNumber: 10012
homeDirectory:
/home/user2
# user3, People, kevin.com
dn: uid=user3,ou=People,
dc
=kevin,
dc
=com
uid: user3
cn: user3
objectClass: account
objectClass: posixAccount
objectClass:
top
objectClass: shadowAccount
userPassword:: a2V2aW4xMjM=
shadowLastChange: 17053
shadowMin: 0
shadowMax: 99999
shadowWarning: 7
loginShell:
/bin/bash
uidNumber: 10013
gidNumber: 10013
homeDirectory:
/home/user3
# search result
search: 2
result: 0 Success
# numResponses: 5
# numEntries: 4
[root@openldap-slave ldap]
# ldapsearch -x -D "cn=Manager,dc=kevin,dc=com" -b "ou=Group,dc=kevin,dc=com" -w 123@ldap
# extended LDIF
#
# LDAPv3
# base <ou=Group,dc=kevin,dc=com> with scope subtree
# filter: (objectclass=*)
# requesting: ALL
#
# Group, kevin.com
dn: ou=Group,
dc
=kevin,
dc
=com
ou: Group
objectClass:
top
objectClass: organizationalUnit
# user1, Group, kevin.com
dn: cn=user1,ou=Group,
dc
=kevin,
dc
=com
objectClass: posixGroup
objectClass:
top
cn: user1
userPassword:: a2V2aW4xMjM=
gidNumber: 10011
# user2, Group, kevin.com
dn: cn=user2,ou=Group,
dc
=kevin,
dc
=com
objectClass: posixGroup
objectClass:
top
cn: user2
userPassword:: a2V2aW4xMjM=
gidNumber: 10012
# user3, Group, kevin.com
dn: cn=user3,ou=Group,
dc
=kevin,
dc
=com
objectClass: posixGroup
objectClass:
top
cn: user3
userPassword:: a2V2aW4xMjM=
gidNumber: 10013
# search result
search: 2
result: 0 Success
# numResponses: 5
# numEntries: 4
由上面slave从节点查看到的数据可知,slave从节点已经将master主节点新导入的输入同步过来了!即主从同步已成功了!
|
登录openldap-slave从节点的phpLDAPadmin,(退出并重新登录master和slave节点的phpLDAPadmin,就能发现上面新导入的数据了)也可以看到从openldap-master主节点同步过来的数据(可以从slave的openldap日志/var/log/slapd/slapd.log文件中查看数据同步情况)

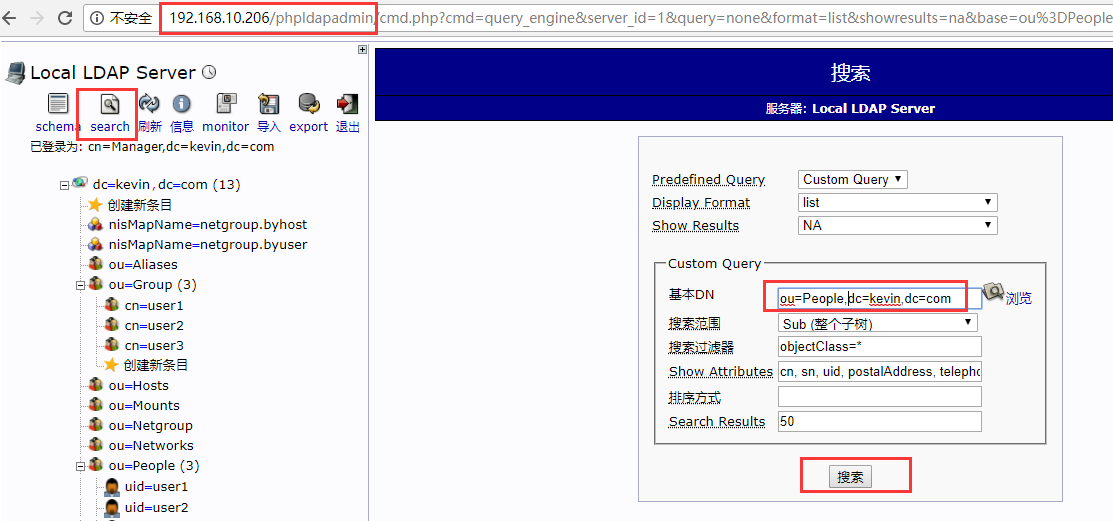

在openldap-master主节点上删除数据,比如删除上面在People组内创建的用户user1和user3
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
|
[root@openldap-master openldap]
# ldapdelete -x -D "cn=Manager,dc=kevin,dc=com" "uid=user1,ou=People,dc=kevin,dc=com" -w ldap@123
[root@openldap-master openldap]
# ldapdelete -x -D "cn=Manager,dc=kevin,dc=com" "uid=user3,ou=People,dc=kevin,dc=com" -w ldap@123
========================================================================
如果命令执行后报错:ldap_bind: Invalid credentials (49)
基本就是由于密码输入不对或ldif文件配置不对造成的
=========================================================================
查看下openldap-master主节点的ldap目录中的以上数据是否删除
[root@openldap-master openldap]
# ldapsearch -x -H ldap://192.168.10.205:389 -b "dc=kevin,dc=com" |grep uid=user1
[root@openldap-master openldap]
# ldapsearch -x -H ldap://192.168.10.205:389 -b "dc=kevin,dc=com" |grep uid=user3
[root@openldap-master openldap]
# ldapsearch -x -H ldap://192.168.10.205:389 -b "dc=kevin,dc=com" |grep uid=user2
dn: uid=user2,ou=People,
dc
=kevin,
dc
=com
然后在openldap-slave从节点上查看,发现从节点的ldap目录中People组内也没有用户user1和user3了
[root@openldap-slave ldap]
# ldapsearch -x -H ldap://192.168.10.206:389 -b "dc=kevin,dc=com" |grep uid=user1
[root@openldap-slave ldap]
# ldapsearch -x -H ldap://192.168.10.206:389 -b "dc=kevin,dc=com" |grep uid=user3
[root@openldap-slave ldap]
# ldapsearch -x -H ldap://192.168.10.206:389 -b "dc=kevin,dc=com" |grep uid=user2
dn: uid=user2,ou=People,
dc
=kevin,
dc
=com
说明主从节点完成了同步!
退出并重新登录openldap-master主节点或openldap-slave从节点的phpLDAPadmin,就能看到删除的数据已经不再了。
|
可以在主节点的phpLDAPadmin的web界面里进行增加、删除、修改等更新操作;可以将phpLDAPadmin左边栏用不到的条目删除(也可以不删除,以备后续使用);可以将phpLDAPadmin中已存在的条目导出Ldif文件格式,将内容复制出来,然后在master节点上编写新的ldif文件(在复制的内容上根据自己的需要修改下即可)。
=========OpenLDAP+Keepalive主主模式(Mirror Mode)高可用环境配置==========
openldap主主模式配置目的
使用openldap本身的配置来完成openldap之间的同步,包括在openldap的主服务器上添加,修改,删除用户时,从服务器上也和主服务器上完成相同的操作。在从服务器上添加,修改,删除用户时,主服务器上也完成一样的操作。从而保证数据在主从openldap服务器上的一致。
openldap主主模式原理
其实现原理如下图,当在主服务器上更新数据时,该更新通过更新日志记录,并将更新复制到从服务器上。当在从服务器上更新数据时,该更新请求将重定向给主服务器,然后主服务器将更新数据复制到从服务器。
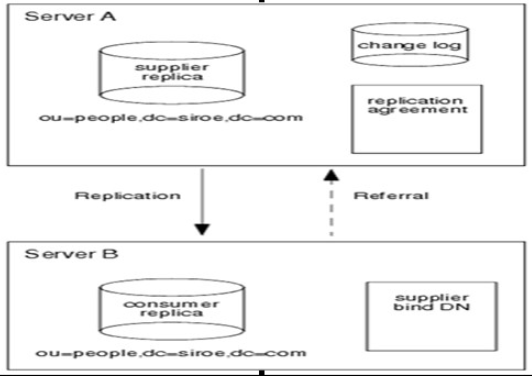
基于上面两台机器192.168.10.205和192.168.10.206安装的openldap环境,现在想要实现keepalived+openldap主主模式(Mirror Mode)模式,配置记录如下:
1)192.168.10.205节点的slapd.conf配置
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
|
[root@openldap-master ~]
# vim /etc/openldap/slapd.conf
.......
modulepath
/usr/lib/openldap
modulepath
/usr/lib64/openldap
......
moduleload syncprov.la
......
database bdb
suffix
"dc=kevin,dc=com"
checkpoint 1024 15
rootdn
"cn=Manager,dc=kevin,dc=com"
......
rootpw {SSHA}b6YpCvRFWAWQdJpueuyzk79VXlikj4Z1
......
loglevel 256
......
index entryCSN,entryUUID
eq
#replication
overlay syncprov
syncprov-checkpoint 100 10
syncprov-sessionlog 100
serverID 1
syncrepl rid=002
provider=ldap:
//192
.168.10.206:389
bindmethod=simple
binddn=
"cn=Manager,dc=kevin,dc=com"
credentials=123@ldap
#填写的是对方机器的openldap的密码,不是自己的openldap密码
searchbase=
"dc=kevin,dc=com"
schemachecking=on
filter=
"(objectClass=*)"
scope=sub
schemachecking=off
type
=refreshAndPersist
retry=
"60 +"
mirrormode on
重新生成该节点的配置文件
[root@openldap-master ~]
# vim /etc/openldap/slapd.conf
[root@openldap-master ~]
# rm -rf /etc/openldap/slapd.d/*
[root@openldap-master ~]
# slaptest -f /etc/openldap/slapd.conf -F /etc/openldap/slapd.d/
config
file
testing succeeded
[root@openldap-master ~]
# slaptest -u
config
file
testing succeeded
[root@openldap-master ~]
# chown -R ldap:ldap /var/lib/ldap/
[root@openldap-master ~]
# chown -R ldap:ldap /etc/openldap/
[root@openldap-master ~]
# service slapd restart
Stopping slapd: [ OK ]
Starting slapd: [ OK ]
[root@openldap-master ~]
# lsof -i:389
COMMAND PID USER FD TYPE DEVICE SIZE
/OFF
NODE NAME
slapd 14047 ldap 7u IPv4 846134 0t0 TCP *:ldap (LISTEN)
slapd 14047 ldap 8u IPv6 846135 0t0 TCP *:ldap (LISTEN)
|
2)192.168.10.206节点的slapd.conf配置
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
|
[root@openldap-slave ~]
# vim /etc/openldap/slapd.conf
.......
modulepath
/usr/lib/openldap
modulepath
/usr/lib64/openldap
......
moduleload syncprov.la
......
database bdb
suffix
"dc=kevin,dc=com"
checkpoint 1024 15
rootdn
"cn=Manager,dc=kevin,dc=com"
......
rootpw {SSHA}X3wlj1uJmB50FM4rNN4869VCeMd92Pcr
......
loglevel 256
......
index entryCSN,entryUUID
eq
#replication
overlay syncprov
syncprov-checkpoint 100 10
syncprov-sessionlog 100
serverID 2
#该ID一定不能跟另一个节点的ID相同
syncrepl rid=002
#该rid一定要跟另一个节点的rid配置相同
provider=ldap:
//192
.168.10.205:389
bindmethod=simple
binddn=
"cn=Manager,dc=kevin,dc=com"
credentials=ldap@123
#填写的是对方机器的openldap的密码,不是自己的openldap密码
searchbase=
"dc=kevin,dc=com"
schemachecking=on
filter=
"(objectClass=*)"
scope=sub
schemachecking=off
type
=refreshAndPersist
retry=
"60 +"
mirrormode on
重新生成该节点的配置文件
[root@openldap-slave ~]
# rm -rf /etc/openldap/slapd.d/*
[root@openldap-slave ~]
# slaptest -f /etc/openldap/slapd.conf -F /etc/openldap/slapd.d/
config
file
testing succeeded
[root@openldap-slave ~]
# slaptest -u
config
file
testing succeeded
[root@openldap-slave ~]
# chown -R ldap:ldap /var/lib/ldap/
[root@openldap-slave ~]
# chown -R ldap:ldap /etc/openldap/
[root@openldap-slave ~]
# service slapd restart
Stopping slapd: [ OK ]
Starting slapd: [ OK ]
[root@openldap-slave ~]
# lsof -i:389
COMMAND PID USER FD TYPE DEVICE SIZE
/OFF
NODE NAME
slapd 30022 ldap 7u IPv4 4984193 0t0 TCP *:ldap (LISTEN)
slapd 30022 ldap 8u IPv6 4984194 0t0 TCP *:ldap (LISTEN)
slapd 30022 ldap 11u IPv4 4984206 0t0 TCP openldap-slave:42138->openldap-master:ldap (ESTABLISHED)
|
3)在192.168.10.205和192.168.10.206节点上各自导入新数据,然后测试主主同步是否生效
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
|
现在192.168.10.205节点上导入新数据
[root@openldap-master ~]
# cat /etc/openldap/people.ldif
dn: uid=ops,ou=People,
dc
=kevin,
dc
=com
uid: ops
cn: ops
objectClass: account
objectClass: posixAccount
objectClass:
top
objectClass: shadowAccount
userPassword: kevin123
shadowLastChange: 17053
shadowMin: 0
shadowMax: 99999
shadowWarning: 7
loginShell:
/bin/bash
uidNumber: 10033
gidNumber: 10033
homeDirectory:
/home/ops
[root@openldap-master ~]
# ldapadd -x -D "cn=Manager,dc=kevin,dc=com" -w ldap@123 -f /etc/openldap/people.ldif
adding new entry
"uid=ops,ou=People,dc=kevin,dc=com"
在192.168.10.206节点上查看自己的ldap目录里是否同步过来数据了
[root@openldap-slave ~]
# ldapsearch -x -D "cn=Manager,dc=kevin,dc=com" -b "ou=People,dc=kevin,dc=com" -w 123@ldap|grep uid=ops
dn: uid=ops,ou=People,
dc
=kevin,
dc
=com
说明从192.168.10.205节点到192.168.10.206节点的数据同步是成功的!
接着在192.168.10.206节点上导入新数据
[root@openldap-slave ~]
# cat /etc/openldap/add.ldif
dn: cn=wangqiuzhe,ou=technology,
dc
=kevin,
dc
=com
cn: wangqiuzhe
description:
man
description: boy
objectclass: person
objectclass: organizationalPerson
objectclass: inetOrgPerson
ou: technology
sn: wang
uid: anan
[root@openldap-slave ~]
# ldapadd -x -D "cn=Manager,dc=kevin,dc=com" -w 123@ldap -f /etc/openldap/add.ldif
adding new entry
"cn=wangqiuzhe,ou=technology,dc=kevin,dc=com"
在192.168.10.205节点上查看自己的ldap目录里是否同步过来数据了
[root@openldap-master ~]
# ldapsearch -x -D "cn=Manager,dc=kevin,dc=com" -b "ou=technology,dc=kevin,dc=com" -w ldap@123|grep cn=wangqiuzhe
dn: cn=wangqiuzhe,ou=technology,
dc
=kevin,
dc
=com
说明从192.168.10.206节点到192.168.10.205节点的数据同步也是成功的!登录各自的phpldapadmin界面里也可以操作数据已测试同步效果。
到此说明,两个节点的openldap主主同步已经完成了!
|
4)在192.168.10.205和192.168.10.206两个节点上均安装keepalived,结合keepalived配置实现vip故障转移,即对外提供一个统一的地址。
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
170
171
172
173
174
175
176
|
keepalived安装(192.168.10.205和192.168.10.206两节点都要操作)
[root@openldap-master ~]
# yum -y install gcc pcre-devel zlib-devel openssl-devel
[root@openldap-master ~]
# cd /usr/local/src/
[root@openldap-master src]
# wget http://www.keepalived.org/software/keepalived-1.3.2.tar.gz
[root@openldap-master src]
# tar -zvxf keepalived-1.3.2.tar.gz
[root@openldap-master src]
# cd keepalived-1.3.2
[root@openldap-master keepalived-1.3.2]
# ./configure && make && make install
[root@openldap-master keepalived-1.3.2]
# cp /usr/local/src/keepalived-1.3.2/keepalived/etc/init.d/keepalived /etc/rc.d/init.d/
[root@openldap-master keepalived-1.3.2]
# cp /usr/local/etc/sysconfig/keepalived /etc/sysconfig/
[root@openldap-master keepalived-1.3.2]
# mkdir /etc/keepalived
[root@openldap-master keepalived-1.3.2]
# cp /usr/local/etc/keepalived/keepalived.conf /etc/keepalived/
[root@openldap-master keepalived-1.3.2]
# cp /usr/local/sbin/keepalived /usr/sbin/
[root@openldap-master keepalived-1.3.2]
# echo "/etc/init.d/keepalived start" >> /etc/rc.local
[root@openldap-master keepalived-1.3.2]
# chkconfig --add keepalived
[root@openldap-master keepalived-1.3.2]
# chkconfig keepalived on
[root@openldap-master keepalived-1.3.2]
# chkconfig --list|grep keepalived
keepalived 0:off 1:off 2:on 3:on 4:on 5:on 6:off
===============配置keepalived.conf(VIP地址为192.168.10.228)=============
接着看下192.168.10.205节点的keepalived配置:
[root@openldap-master ~]
# cp /etc/keepalived/keepalived.conf /etc/keepalived/keepalived.conf.bak
[root@openldap-master ~]
# vim /etc/keepalived/keepalived.conf
! Configuration File
for
keepalived
global_defs {
notification_email {
root@localhost
}
notification_email_from root@localhost
smtp_server localhost
smtp_connect_timeout 30
router_id LDAP-205
}
vrrp_script chk_ldap_port {
script
"/opt/chk_ldap.sh"
interval 2
weight -5
fall 2
rise 1
}
vrrp_instance VI_1 {
state MASTER
interface eth0
mcast_src_ip 192.168.10.205
virtual_router_id 51
priority 101
advert_int 1
authentication {
auth_type PASS
auth_pass 1111
}
virtual_ipaddress {
192.168.10.208
}
track_script {
chk_ldap_port
}
}
编写openldap监控脚本
[root@openldap-master ~]
# vim /opt/chk_ldap.sh
#!/bin/bash
counter=$(
ps
-C slapd --no-heading|
wc
-l)
if
[
"${counter}"
=
"0"
];
then
/etc/init
.d
/slapd
start
sleep
2
counter=$(
ps
-C slapd --no-heading|
wc
-l)
if
[
"${counter}"
=
"0"
];
then
/etc/init
.d
/keepalived
stop
fi
fi
[root@openldap-master ~]
# chmod 755 /opt/chk_ldap.sh
=====================================================
接着看下192.168.10.206的keepalived.conf配置
[root@openldap-slave ~]
# cp /etc/keepalived/keepalived.conf /etc/keepalived/keepalived.conf.bak
[root@openldap-slave ~]
# vim /etc/keepalived/keepalived.conf
! Configuration File
for
keepalived
global_defs {
notification_email {
root@localhost
}
notification_email_from root@localhost
smtp_server localhost
smtp_connect_timeout 30
router_id LDAP-206
}
vrrp_script chk_ldap_port {
script
"/opt/chk_ldap.sh"
interval 2
weight -5
fall 2
rise 1
}
vrrp_instance VI_1 {
state BACKUP
interface eth0
mcast_src_ip 192.168.10.206
virtual_router_id 51
priority 99
advert_int 1
authentication {
auth_type PASS
auth_pass 1111
}
virtual_ipaddress {
192.168.10.208
}
track_script {
chk_ldap_port
}
}
编写openldap监控脚本
[root@openldap-slave ~]
# vim /opt/chk_ldap.sh
#!/bin/bash
counter=$(
ps
-C slapd --no-heading|
wc
-l)
if
[
"${counter}"
=
"0"
];
then
/etc/init
.d
/slapd
start
sleep
2
counter=$(
ps
-C slapd --no-heading|
wc
-l)
if
[
"${counter}"
=
"0"
];
then
/etc/init
.d
/keepalived
stop
fi
fi
[root@openldap-slave ~]
# chmod 755 /opt/chk_ldap.sh
==================================================
接着启动192.168.10.205 和 192.168.10.206两节点的keepalived服务
[root@openldap-master ~]
# /etc/init.d/keepalived start
Starting keepalived: [ OK ]
[root@openldap-master ~]
# ps -ef|grep keepalived
root 17790 1 0 16:15 ? 00:00:00 keepalived -D
root 17791 17790 0 16:15 ? 00:00:00 keepalived -D
root 17792 17790 0 16:15 ? 00:00:00 keepalived -D
root 17943 13447 0 16:16 pts
/0
00:00:00
grep
keepalived
[root@openldap-master ~]
# ip addr
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN
link
/loopback
00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1
/8
scope host lo
inet6 ::1
/128
scope host
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP qlen 1000
link
/ether
52:54:00:b1:9c:93 brd ff:ff:ff:ff:ff:ff
inet 192.168.10.205
/24
brd 192.168.10.255 scope global eth0
inet 192.168.10.208
/32
scope global eth0
inet6 fe80::5054:ff:feb1:9c93
/64
scope link
valid_lft forever preferred_lft forever
[root@openldap-slave ~]
# /etc/init.d/keepalived start
Starting keepalived: [ OK ]
[root@openldap-slave ~]
# ps -ef|grep keepalived
root 2635 1 0 16:11 ? 00:00:00 keepalived -D
root 2636 2635 0 16:11 ? 00:00:00 keepalived -D
root 2637 2635 0 16:11 ? 00:00:00 keepalived -D
root 2650 24277 0 16:11 pts
/0
00:00:00
grep
keepalived
[root@openldap-slave ~]
# ip addr
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN
link
/loopback
00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1
/8
scope host lo
inet6 ::1
/128
scope host
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP qlen 1000
link
/ether
52:54:00:
dd
:84:6b brd ff:ff:ff:ff:ff:ff
inet 192.168.10.206
/24
brd 192.168.10.255 scope global eth0
inet6 fe80::5054:ff:fedd:846b
/64
scope link
valid_lft forever preferred_lft forever
由上面信息可以看出,目前的VIP资源在192.168.10.205节点机器上
|
5)故障切换测试
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
|
关闭192.168.10.205和192.168.10.206两个节点的slapd服务,默认每2秒钟会进行一次脚本检查(
/opt/chk_ldap
.sh),当
检查到slapd服务关闭后,会第一时间执行
/opt/chk_ldap
.sh脚本去自启动slapd服务。
[root@openldap-master ~]
# /etc/init.d/slapd stop
Stopping slapd: [ OK ]
[root@openldap-master ~]
# ps -ef|grep slapd
root 18755 13447 0 16:20 pts
/0
00:00:00
grep
slapd
[root@openldap-master ~]
# ps -ef|grep slapd
ldap 18795 1 0 16:20 ? 00:00:00
/usr/sbin/slapd
-h ldap:
///
ldapi:
///
-u ldap
root 18803 13447 0 16:20 pts
/0
00:00:00
grep
slapd
当发现slapd服务自启动失败时,就会自动
kill
掉自己的keepalived服务,从而将VIP资源自动切换到另一个节点上。
关闭192.168.10.205节点的keepalived服务,会发现VIP资源自动切换到192.168.10.206节点上
[root@openldap-master ~]
# /etc/init.d/keepalived stop
Stopping keepalived: [ OK ]
[root@openldap-master ~]
# ps -ef|grep keepalived
root 19074 13447 0 16:22 pts
/0
00:00:00
grep
keepalived
[root@openldap-master ~]
# ip addr
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN
link
/loopback
00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1
/8
scope host lo
inet6 ::1
/128
scope host
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP qlen 1000
link
/ether
52:54:00:b1:9c:93 brd ff:ff:ff:ff:ff:ff
inet 192.168.10.205
/24
brd 192.168.10.255 scope global eth0
inet6 fe80::5054:ff:feb1:9c93
/64
scope link
valid_lft forever preferred_lft forever
[root@openldap-slave ~]
# ip addr
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN
link
/loopback
00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1
/8
scope host lo
inet6 ::1
/128
scope host
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP qlen 1000
link
/ether
52:54:00:
dd
:84:6b brd ff:ff:ff:ff:ff:ff
inet 192.168.10.206
/24
brd 192.168.10.255 scope global eth0
inet 192.168.10.208
/32
scope global eth0
inet6 fe80::5054:ff:fedd:846b
/64
scope link
valid_lft forever preferred_lft forever
当192.168.10.205节点的keepalived服务恢复后,VIP资源就会再次切换回来
[root@openldap-master ~]
# /etc/init.d/keepalived start
Starting keepalived: [ OK ]
[root@openldap-master ~]
# ps -ef|grep keepalived
root 19084 1 0 16:22 ? 00:00:00 keepalived -D
root 19085 19084 0 16:22 ? 00:00:00 keepalived -D
root 19087 19084 0 16:22 ? 00:00:00 keepalived -D
root 19099 13447 0 16:23 pts
/0
00:00:00
grep
keepalived
[root@openldap-master ~]
# ip addr
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN
link
/loopback
00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1
/8
scope host lo
inet6 ::1
/128
scope host
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP qlen 1000
link
/ether
52:54:00:b1:9c:93 brd ff:ff:ff:ff:ff:ff
inet 192.168.10.205
/24
brd 192.168.10.255 scope global eth0
inet 192.168.10.208
/32
scope global eth0
inet6 fe80::5054:ff:feb1:9c93
/64
scope link
valid_lft forever preferred_lft forever
这样,192.168.10.205和192.168.10.206两个节点就能对外提供统一的地址:192.168.10.208。
不管是在哪个节点上更新的数据,在客户端连接192.168.10.208的vip地址都能访问到。
注意:
如果192.168.10.205和192.168.10.206两个节点的openldap登录密码不一致,那么:
当VIP在192.168.10.205节点上时,使用192.168.10.208地址访问phpldapadmin,密码就是192.168.10.205节点的openldap密码
当VIP在192.168.10.206节点上时,使用192.168.10.208地址访问phpldapadmin,密码就是192.168.10.206节点的openldap密码
可以在两个节点上导入新数据,然后在客户端通过192.168.10.208访问ldap,测试下是否能读到新数据。
|