实验目的:
通过实验可以掌握:
a. 标准ACL
b. 扩展ACLL
c. 基于时间ACL调试
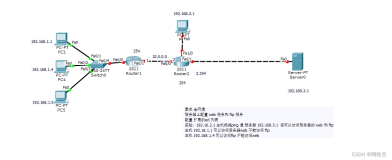
实验拓扑:
四台路由器,连接及IP配置如图所示,使用了循回口模拟内部网络。
要求说明:
1.不允许R1访问R4及其内部网络
2.不允许10.1.1.0网段在工作时间(周一至同五,8:00-18:00)内ping或者telnet R4及其内部网络
3.不允许R2 ping R4
4.不允许10.2.2.0网段访问R4及其内部网络
5.使用OSPF动态路由协议
本实验在模拟器下进行。
具体配置如下:
1.基本配置及密码设置
R1,R2,R3,R4启动后,首先进行如下配置
Router#
Router#conf terminal
Router(config)#no ip domain look
Router(config)#lin cons 0
Router(config-line)# logging synchronous
Router(config-line)#exec-time 0 0
Router(config-line)#exit
Router(config)#
Router(config)#enable password cisco
Router(config)#line vty 0 4
Router(config-line)#password ciscovty
Router(config-line)#login
Router(config-line)#hostname RX //(4台路由器分别命令为R1,R2,R3,R4)
2.配置接口地址,这个就不多说了,以R3为例
R3(config)#
R3(config)#int f1/1
R3(config-if)#ip address 192.168.13.3 255.255.255.0
R3(config-if)#no shutdown
R3(config-if)#int f1/3
R3(config-if)#ip address 192.168.23.3 255.255.255.0
R3(config-if)#no shutdown
R3(config-if)#int s3/0
R3(config-if)#ip address 172.16.34.3 255.255.255.0
R3(config-if)#clock rate 64000
R3(config-if)#no shutdown
R3(config-if)#
3.设置OSPF路由协议
R1(config)#
R1(config)#router ospf 10
R1(config-router)#network 10.1.1.0 0.0.0.255 area 0
R1(config-router)#network 192.168.13.0 0.0.0.255 area 0
R1(config-router)#exit
R1(config)#
R2(config)#
R2(config)#router ospf 20
R2(config-router)#network 10.2.2.0 0.0.0.255 area 0
R2(config-router)#network 192.168.23.0 0.0.0.255 area 0
R2(config-router)#exit
R2(config)#
R3(config)#
R3(config)#router ospf 30
R3(config-router)#network 10.3.3.0 0.0.0.255 area 0
R3(config-router)#network 192.168.13.0 0.0.0.255 area 0
R3(config-router)#network 192.168.23.0 0.0.0.255 area 0
R3(config-router)#network 172.16.34.0 0.0.0.255 area 0
R3(config-router)#exit
R3(config)#
R4(config)#
R4(config)#router ospf 40
R4(config-router)#network 10.4.4.0 0.0.0.255 area 0
R4(config-router)#network 172.16.34.0 0.0.0.255 area 0
R4(config-router)#exit
R4(config)#
4.在R3上查看学到的路由
以下数据表明,整个网络已经互通的,经测试各网段间可相互ping通。
R3#
R3#show ip route
Codes: C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
o - ODR, P - periodic downloaded static route
Gateway of last resort is not set
C 192.168.13.0/24 is directly connected, FastEthernet1/1
172.16.0.0/24 is subnetted, 1 subnets
C 172.16.34.0 is directly connected, Serial3/0
10.0.0.0/8 is variably subnetted, 4 subnets, 2 masks
O 10.2.2.2/32 [110/2] via 192.168.23.2, 00:00:43, FastEthernet1/3
C 10.3.3.0/24 is directly connected, Loopback0
O 10.1.1.1/32 [110/2] via 192.168.13.1, 00:00:43, FastEthernet1/1
O 10.4.4.4/32 [110/65] via 172.16.34.4, 00:00:43, Serial3/0
C 192.168.23.0/24 is directly connected, FastEthernet1/3
R3#
5.设置标准ACL,禁止R1和10.2.2.0/24访问R4及其内部网络
该标准ACL应用到R4的S3/0端口入方向
R4(config)#
R4(config)#access-list 10 deny host 192.168.13.1
R4(config)#access-list 10 deny 10.2.2.0 0.0.0.255
R4(config)#access-list 10 permit any
R4(config)#int s3/0
R4(config-if)#ip access-group 10 in
R4(config-if)#end
R4#
6.设置扩展ACL,禁止R2 ping R4,禁止10.1.1.0/24网段在工作时间内 ping或者telnet R4及10.4.4.0/24网段
该扩展ACL应用到R3的S3/0端口出方向
R3(config)#
R3(config)#time-range time //定义时间范围
R3(config-time-range)#periodic weekdays 8:00 to 18:00
R3(config-time-range)#exit
R3(config)#access-list 100 deny icmp host 192.168.23.2 host 172.16.34.4
R3(config)#access-list 100 deny icmp 10.1.1.0 0.0.0.255 any time-range time
R3(config)#access-list 100 deny tcp 10.1.1.0 0.0.0.255 any eq telnet time-range time
R3(config)#access-list 100 permit ip any any
R3(config)#int s3/0
R3(config-if)#ip access-group 100 out
R3(config-if)#end
R3#
7.查看ACL
R3#
R3#show time-range
time-range entry: time (active)
periodic weekdays 8:00 to 18:00
used in: IP ACL entry
used in: IP ACL entry
R3#
R3#show access-lists
Extended IP access list 100
10 deny icmp host 192.168.23.2 host 172.16.34.4 (16 matches)
20 deny icmp 10.1.1.0 0.0.0.255 any time-range time (active) (16 matches)
30 deny tcp 10.1.1.0 0.0.0.255 any eq telnet time-range time (active) (6 matches)
40 permit ip any any (133 matches)
R3#
R4#
R4#show access-lists
Standard IP access list 10
10 deny 192.168.13.1
20 deny 10.2.2.0, wildcard bits 0.0.0.255 (19 matches)
30 permit any (737 matches)
R4#
8.测试
查看R3学到的路由条目
R3#
R3#show ip route
Codes: C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
o - ODR, P - periodic downloaded static route
Gateway of last resort is not set
C 192.168.13.0/24 is directly connected, FastEthernet1/1
172.16.0.0/24 is subnetted, 1 subnets
C 172.16.34.0 is directly connected, Serial3/0
10.0.0.0/8 is variably subnetted, 4 subnets, 2 masks
O 10.2.2.2/32 [110/2] via 192.168.23.2, 00:03:00, FastEthernet1/3
C 10.3.3.0/24 is directly connected, Loopback0
O 10.1.1.1/32 [110/2] via 192.168.13.1, 00:03:00, FastEthernet1/1
O 10.4.4.4/32 [110/65] via 172.16.34.4, 00:03:00, Serial3/0
C 192.168.23.0/24 is directly connected, FastEthernet1/3
以上表明R3学到的路由跟先前查看的一样,经测试,R3能ping通网络内的所有地址
======================================================================
R1 ping R4
R1#ping 172.16.34.4
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 172.16.34.4, timeout is 2 seconds:
U.U.U
Success rate is 0 percent (0/5)
---------------------------------------------------
R1 telnet R4
R1#telnet 172.16.34.4
Trying 172.16.34.4 ...
% Destination unreachable; gateway or host down
---------------------------------------------------
R1 ping 10.4.4.4
R1#ping 10.4.4.4
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.4.4.4, timeout is 2 seconds:
U.U.U
Success rate is 0 percent (0/5)
以上表明,R1不能访问R4及其内部网段
======================================================================
(在R3上通过clock set hh:mm:ss moon date year 命令设置时钟,通过show clock命令查看时钟)
10.1.1.1 在非工作时间—16:30:06.587 UTC Sun Nov 21 2010 内—ping R4
R1#ping 172.16.34.4 source 10.1.1.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 172.16.34.4, timeout is 2 seconds:
Packet sent with a source address of 10.1.1.1
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 16/48/92 ms
---------------------------------------------------
10.1.1.1 在非工作时间—18:31:42.871 UTC Mon Nov 22 2010 内—telnet R4
R1#telnet 172.16.34.4 /source-interface lo0
Trying 172.16.34.4 ... Open
---------------------------------------------------
10.1.1.1 在工作时间—16:30:16.531 UTC Mon Nov 22 2010 内—ping 10.4.4.4
R1#ping 10.4.4.4 source 10.1.1.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.4.4.4, timeout is 2 seconds:
Packet sent with a source address of 10.1.1.1
U.U.U
Success rate is 0 percent (0/5)
---------------------------------------------------
10.1.1.1 在工作时间—16:32:04.331 UTC Mon Nov 22 2010 内—telnet R4
R1#telnet 172.16.34.4 /source-interface lo0
Trying 172.16.34.4 ...
% Destination unreachable; gateway or host down
以上表明,10.1.1.0网段,在工作时间内不可以ping或者telnet R4及其内部网络
======================================================================
R2 ping R4
R2#ping 172.16.34.4
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 172.16.34.4, timeout is 2 seconds:
U.U.U
Success rate is 0 percent (0/5)
---------------------------------------------------
R2 ping 10.4.4.4
R2#ping 10.4.4.4
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.4.4.4, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 16/58/120 ms
---------------------------------------------------
R2 telnet R4
R2#telnet 172.16.34.4
Trying 172.16.34.4 ... Open
以上表明,R2不能pingR4,但可以telnetR4,并且能与R4内部网络进行正常通信
======================================================================
10.2.2.2 ping R4
R2#ping 172.16.34.4 source 10.2.2.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 172.16.34.4, timeout is 2 seconds:
Packet sent with a source address of 10.2.2.2
U.U.U
Success rate is 0 percent (0/5)
---------------------------------------------------
10.2.2.2 ping 10.4.4.4
R2#ping 10.4.4.4 source 10.2.2.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.4.4.4, timeout is 2 seconds:
Packet sent with a source address of 10.2.2.2
U.U.U
Success rate is 0 percent (0/5)
---------------------------------------------------
10.2.2.2 telnet 172.16.34.4
R2#telnet 172.16.34.4 /source-interface lo0
Trying 172.16.34.4 ...
% Destination unreachable; gateway or host down
以上表明,10.2.2.0网段不能访问R4及其内部网段
=============================================================
本文转自Sunshyfangtian 51CTO博客,原文链接:http://blog.51cto.com/sunshyfangtian/428784,如需转载请自行联系原作者